21
Mar
On 28th of February, I’ve sent a short summary to lkrg-users mailing list (https://www.openwall.com/lists/lkrg-users/2020/02/28/1) regarding recent Linux kernel XFRM UAF exploit dropped by Vitaly Nikolenko. I believe it is worth reading and I’ve decided to reference it on my blog as well:
Read moreSome time ago I’ve found an interesting memory corruption bug (via integer overflow) in the mechanism responsible for parsing XMSS private keys. This bug is addressed in the latest OpenSSH released version (8.1) and more details about the bug can be found here:
CVE-2019-16905 – OpenSSH Pre-Auth XMSS Integer Overflow
Best regards,
Adam
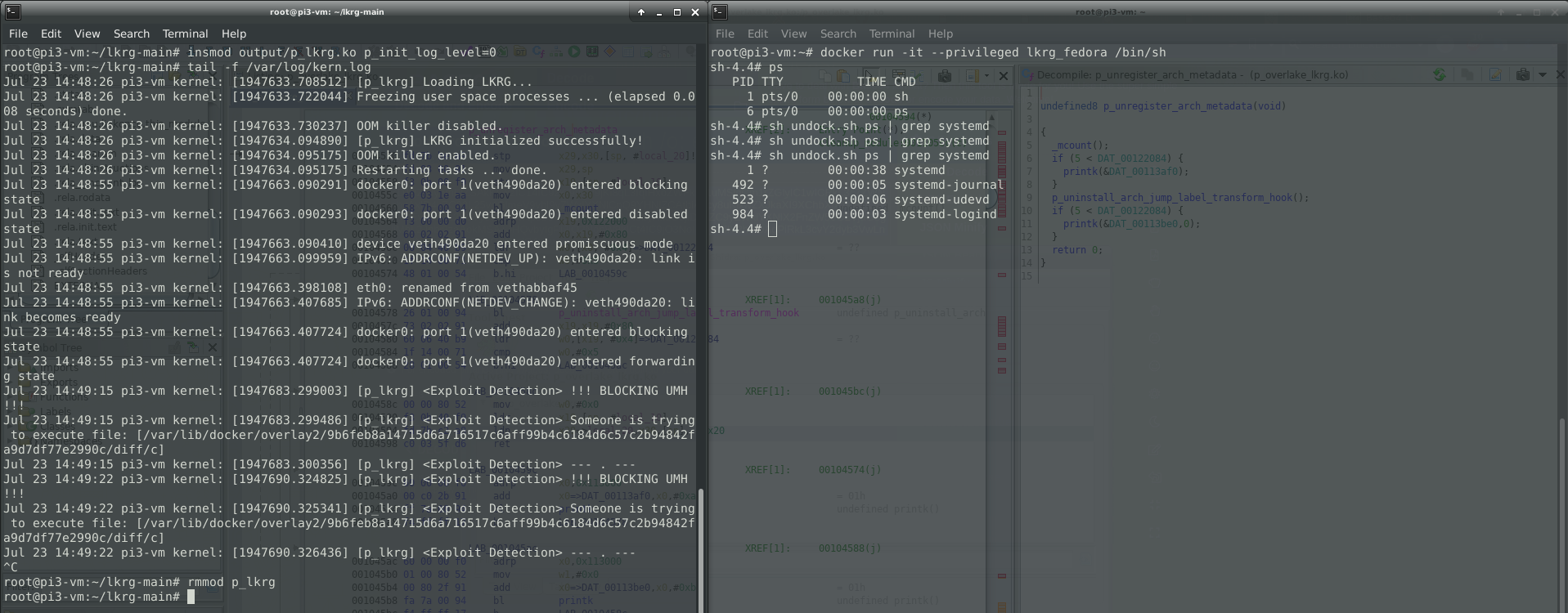
Felix Wilhelm recently tweeted a Proof of Concept (PoC) of container escape abusing release agent for cgroup v1.
To be able to perform the attack, container was run with the “–privileged” flag which is not a setup for security anyway. When using this flag, containers have full access to all devices and lack restrictions from seccomp, AppArmor, and Linux capabilities. Nevertheless, “–privileged” flag is just a simplification of the necessary requirements for this attack, which is SYS_ADMIN capability for the container itself, as well as VFS for cgroup v1 mount with the read and write permission.
Felix was able to inject a custom command into the mechanism known as a “notify_on_release” in cgroup v1. When the last task in a cgroup leaves it, a release agent is executed by the kernel via call_usermodehelper_exec() (UserModeHelper – UMH) mechanism. Since the kernel is doing ‘clean-up’, UMH is executed on the host outside of the namespace / container.
More information about release_agent can be found here:
https://www.kernel.org/doc/Documentation/cgroup-v1/cgroups.txt
Linux Kernel Runtime Guard (LKRG) has functionality of limiting an UMH interface. By default, it is allowed to execute only LKRG’s whitelisted programs. For some people it might be not enough and in that case LKRG has an ability to fully lock UMH and nothing can be executed via this interface. This might break things if your distro uses UMH to invoke any programs e.g. if you are using release_agent 😉
You can see how LKRG can save you by preventing and detecting Felix’s container escape (based on UMH) here:
Thanks,
Adam
14
May
Some time ago I took a look at i915 driver a bit. During my research I had found a few problems which had been fixed. Today (14th of May 2019), Intel announced the fix for reported security bug in i915 driver when Graphical Virtualization (GVT) is enabled under KVM (CVE-2019-11085 / INTEL-SA-00249). To be more specific, Intel’s vGPU driver allows for mappinng of arbitrary physical page into the context of calling process via mmap()
Additionally, Linux kernel community fixed two other bugs:
“[1/2] drm/i915: Prevent a race during I915_GEM_MMAP ioctl with WC set”
https://patchwork.kernel.org/patch/10750161/
“[2/2] drm/i915: Handle vm_mmap error during I915_GEM_MMAP ioctl with WC set”
https://patchwork.kernel.org/patch/10750163/
These bugs are pretty interesting from the pure research perspective so it is worth to take a look at the published patches.
Thanks,
Adam
3
Apr
One of the author of Windows Internals (Andrea Allievi) asked me and my friend David Kaplan if we could write a section about System Guard Runtime Attestation for their book. We’ve written about 3-4 pages describing internals of that project which we fully designed. Our section will be included in Windows Internals 7th edition part 2 (release date around August 2019):
Windows Defender System Guard Runtime Attestation (SGRA / SGRM) is internally known as a project Octagon which me and Dave fully designed and implemented together with Octagon v-team. Octagon is now included in every Windows build and first implementation of this new technology has been introduced in Windows 10 April 2018 Update (RS4). You can learn more about this project here:
Best regards,
Adam
19
Feb
Hi,
We’ve just announced a new version of LKRG 0.6! This release is… BIG! A few words why:
- We've introduced a new mitigation features which we call "poor's man CFI" (pCFI). It is designed to "catch" exploits which corrupts stack pointer to execute ROP and/or execute code not from the official .text section of the kernel (e.g. from the heap page, or user-mode page)
- We are using pCFI to enforce SMEP bit in CR4 and WP bit in CR0. If attacker disables one of that bits, LKRG will re-enable it again
- We've locked-down usermodehelper (UMH) interface - it will kill "class" of exploit abusing UMH
- We've completely rewrote *_JUMP_LABEL support - now it is independent of CPU architecture and can work on any CPU. Previously it was designed for x86 arch. New *_JUMP_LABEL support logic significantly reduce memory footprint, remove whitelisting, simplifies some algorithms and so on...
- We've introduce early boot systemd script/unit. Now you can easily manage LKRG service as any other service in the system. Systemd is the only init system which we support for now, but there is no reason to add support for other systems.
- We've fixed a few known problems with LKRG and made it more stable
- We've made all necessary changes to run LKRG on latest kernels
- A few more!
It’s a big release with a lot of changes. Full announcement can be found here:
https://www.openwall.com/lists/announce/2019/02/19/1
Next, I would like to work on ARM support for LKRG. Stay tuned….
30
Aug
I believe this is one of the most stable release so far 🙂
The full announcement can be found here:
http://www.openwall.com/lists/announce/2018/08/30/1
I’m already working on the next version of LKRG which will include (among others) *_JUMP_LABEL support for modules as well (for now LKRG supports it just for kernel core .text). This is a big, complicate and heavy change and that’s why we decided to announce 0.4 now since we wanted to have a stable release.
Thanks,
Adam
27
Mar
LKRG 0.2 was just released and the announcement note can be found here:
http://openwall.com/lists/announce/2018/03/27/1
9
Feb
LKRG 0.1 was just released:
The change log is as follows:
Read more
30
Jan

I’m happy to announce that my moonlight project is finally released. Thanks to Alexander Peslyak (a.k.a. Solar Designer) it is available through Openwall.
Linux Kernel Runtime Guard (LKRG) is a loadable kernel module that performs runtime integrity checking of the Linux kernel and detection of security vulnerability exploits against the kernel. As controversial as this concept is, LKRG attempts to post-detect and hopefully promptly respond to unauthorized modifications to the running Linux kernel (integrity checking) or to credentials (such as user IDs) of the running processes (exploit detection). For process credentials, LKRG attempts to detect the exploit and take action before the kernel would grant the process access (such as open a file) based on the unauthorized credentials. You can download the current experimental version of LKRG at its brand new homepage:
LKRG has been in (re-)development for a couple of years, and builds upon one of my prior’s experience with a related project in 2011 (for CERN).
Official announcement had been made by Openwall and it can be read here:
http://www.openwall.com/lists/announce/2018/01/29/1
A lot of useful technical information about LKRG can be found on Openwall wiki page:
http://openwall.info/wiki/p_lkrg/Main
If you would like to support LKRG, you are very welcome to do so 😉 It can be done via Patreon website here:
https://www.patreon.com/p_lkrg
Best regards,
Adam ‘pi3’ Zabrocki