Today I’ve received strange mail:
— CUT —
Date: Thu, 01 Sep 2011 09:11:00 +0200
From: gayroobaoll <gayroobaoll@o2.pl>
To: pi3@itsec.pl
Subject:
Chcesz, http://facebook.com/100002779484440
— CUT —
As we can see, there is no subject, mail include link to someone’s facebook profile and has got only one Polish world (yes, this is attack for the Polish ppl). “Chcesz” means “Do you want”. Strange, dosn’t it? Mail was send from the Polish portal (o2.pl) – free mails.
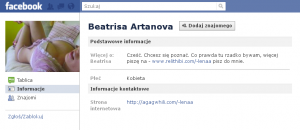
OK 😉 Let’s check this profile…
Hm… interesting 😉 In the section “About” we can find Polish sentence: “Cześć. Chcesz się poznać. Co prawda tu rzadko bywam, więcej piszę na – www.relithibi.com/-lenaa pisz do mnie.” which can be translated to: “Hi. I want to meet you. To be honest, I’m here very rarely, I’m more active here – www.relithibi.com/-lenaa contact with me.” But in the section personal web page we can find different link:
http://agagwhili.com/-lenaa
But this two different URLs go to the same site http://randkipl.com/user.php?page=id&id=16112
OK. What is important here? Anything what we can press on this site forward us to the registration form 😉 On the left site of this page we can see smth like chat box, but it isn’t. This is static talk (maybe sniffed somewhere else) which is always the same. Whenever we visit this page we can see exactly the same talk and sentence sent from the same nicknames. This talk suggest of course sex propositions 😉 But what is important this site detect from which IP address we visit this page and tries to get the possible city from where our IP are and resolve the name of the city and put to the chat box 😉 This is nice social engineering trick 😉 The same situation is in the middle of the site, where is information about profile which we visit. Of course the city name is the same which page detect and the same situation is with the country 😉 Of course in this profile is written that this woman are looking for a men who want to have sex with her 😉
Of course site tries to remember visitors (cookies) and not change so often the city name when we use different IPs.
OK. So I thing this is good moment to check in more details the email which I received. Here is full headers:
— CUT —
Return-Path: <gayroobaoll@o2.pl>
X-Original-To: pi3@itsec.pl
Delivered-To: pi3@itsec.pl
Received: by itsec.pl (Postfix, from userid 1004)
id 97D164CE13; Thu, 1 Sep 2011 09:00:43 +0200 (CEST)
X-Spam-Checker-Version: SpamAssassin 3.3.2 (2011-06-06) on itsec.pl
X-Spam-Level:
X-Spam-Status: No, score=-1.9 required=5.0 tests=BAYES_00,FREEMAIL_FROM,
RCVD_IN_DNSWL_NONE,SPF_PASS,TVD_SPACE_RATIO,T_TO_NO_BRKTS_FREEMAIL
autolearn=ham version=3.3.2
Received: from mailout1.go2.pl (mailout1.go2.pl [193.17.41.11])
by itsec.pl (Postfix) with ESMTP id 84CF931F96
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:00:24 +0200 (CEST)
Received: from mailout1.go2.pl (unknown [10.0.0.103])
by mailout1.go2.pl (Postfix) with ESMTP id BEDA05D5158
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:11:01 +0200 (CEST)
Received: from o2.pl (unknown [10.0.0.40])
by mailout1.go2.pl (Postfix) with SMTP
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:11:01 +0200 (CEST)
Subject:
From: gayroobaoll <gayroobaoll@o2.pl>
To: pi3@itsec.pl
Mime-Version: 1.0
Message-ID: <1a68707d.72ac5cea.4e5f3004.83a38@o2.pl>
Date: Thu, 01 Sep 2011 09:11:00 +0200
X-Originator: 115.132.51.92
Content-Type: text/plain; charset=”UTF-8″
Content-Transfer-Encoding: quoted-printable
— CUT —
The real IP address of someone/something who sent this mail is: 115.132.51.92
This IP address alive and reply for ICMP-echo message:
— CUT —
# ping 115.132.51.92
PING 115.132.51.92 (115.132.51.92) 56(84) bytes of data.
64 bytes from 115.132.51.92: icmp_req=1 ttl=50 time=365 ms
64 bytes from 115.132.51.92: icmp_req=2 ttl=50 time=363 ms
64 bytes from 115.132.51.92: icmp_req=3 ttl=50 time=362 ms
^C
— 115.132.51.92 ping statistics —
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 362.722/363.863/365.174/1.225 ms
— CUT —
whois database:
— CUT —
# whois 115.132.51.92
% [whois.apnic.net node-2]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
inetnum: 115.132.0.0 – 115.135.255.255
netname: ADSLSTREAMYX
descr: CORE IP NETWORK DEVELOPMENT,
descr: TELEKOM MALAYSIA BERHAD
country: MY
admin-c: SM135-AP
tech-c: EAK2-AP
status: ALLOCATED PORTABLE
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
remarks: This object can only be updated by APNIC hostmasters.
remarks: To update this object, please contact APNIC
remarks: hostmasters and include your organisation’s account
remarks: name in the subject line.
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
changed: hm-changed@apnic.net 20080805
mnt-by: APNIC-HM
mnt-lower: MAINT-AP-STREAMYX
changed: hm-changed@apnic.net 20080919
source: APNIC
person: Siti Fuwaizah Mohd. Ghazali
nic-hdl: SM135-AP
e-mail: tm_osc@tmnet.com.my
address: Telekom Malaysia Berhad
address: Jalan Pantai Baru, Kuala Lumpur.
phone: +603-83185434
fax-no: +603-22402126
country: MY
changed: fuwaizah@tm.com.my 20090402
mnt-by: TM-NET-AP
abuse-mailbox: abuse@tm.net.my
notify: tmcops@tmnet.com.my
source: APNIC
person: EMRAN AHMED KAMAL
nic-hdl: EAK2-AP
e-mail: ssc@tmnet.com.my
address: Telekom Malaysia
address: Jalan Pantai Baru, Kuala Lumpur.
phone: +6-03-83185434
fax-no: +6-03-22402126
country: MY
changed: fuwaizah@tm.net.my 20080918
mnt-by: TM-NET-AP
abuse-mailbox: abuse@tm.net.my
source: APNIC
— CUT —
So… of course IP address is “somewhere” 😉 In this case Malaysia Telekom is owner. Greetings for Polish ppl in Malaysia ;p xprobe2 says this is Apple machine:
— CUT —
# xprobe2 -v -r 115.132.51.92
Xprobe2 v.0.3 Copyright (c) 2002-2005 fyodor@o0o.nu, ofir@sys-security.com, meder@o0o.nu
[+] Target is 115.132.51.92
[+] Loading modules.
[+] Following modules are loaded:
[x] [1] ping:icmp_ping – ICMP echo discovery module
[x] [2] ping:tcp_ping – TCP-based ping discovery module
[x] [3] ping:udp_ping – UDP-based ping discovery module
[x] [4] infogather:ttl_calc – TCP and UDP based TTL distance calculation
[x] [5] infogather:portscan – TCP and UDP PortScanner
[x] [6] fingerprint:icmp_echo – ICMP Echo request fingerprinting module
[x] [7] fingerprint:icmp_tstamp – ICMP Timestamp request fingerprinting module
[x] [8] fingerprint:icmp_amask – ICMP Address mask request fingerprinting module
[x] [9] fingerprint:icmp_port_unreach – ICMP port unreachable fingerprinting module
[x] [10] fingerprint:tcp_hshake – TCP Handshake fingerprinting module
[x] [11] fingerprint:tcp_rst – TCP RST fingerprinting module
[x] [12] fingerprint:smb – SMB fingerprinting module
[x] [13] fingerprint:snmp – SNMPv2c fingerprinting module
[+] 13 modules registered
[+] Initializing scan engine
[+] Running scan engine
[-] ping:tcp_ping module: no closed/open TCP ports known on 115.132.51.92. Module test failed
[-] ping:udp_ping module: no closed/open UDP ports known on 115.132.51.92. Module test failed
[-] No distance calculation. 115.132.51.92 appears to be dead or no ports known
[+] Host: 115.132.51.92 is up (Guess probability: 50%)
[+] Target: 115.132.51.92 is alive. Round-Trip Time: 0.36246 sec
[+] Selected safe Round-Trip Time value is: 0.72492 sec
[-] fingerprint:tcp_hshake Module execution aborted (no open TCP ports known)
[-] fingerprint:smb need either TCP port 139 or 445 to run
[-] fingerprint:snmp: need UDP port 161 open
[+] Primary guess:
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.7” (Guess probability: 100%)
[+] Other guesses:
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.8” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.9” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.4.0” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.4.1” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.08 EEPROM F.08.20” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.08 EEPROM F.08.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.01 EEPROM F.08.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM A.05.03 EEPROM A.05.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM A.03.17 EEPROM A.04.09” (Guess probability: 100%)
[+] Cleaning up scan engine
[+] Modules deinitialized
[+] Execution completed.
— CUT —
OK. So let’s check who register randkipl.com domain:
— CUT —
Domain Name: RANDKIPL.COM
Registrar: DIRECTI INTERNET SOLUTIONS PVT. LTD. D/B/A PUBLICDOMAINREGISTRY.COM
Whois Server: whois.PublicDomainRegistry.com
Referral URL: http://www.PublicDomainRegistry.com
Name Server: NS1.REG.RU
Name Server: NS2.REG.RU
Status: clientTransferProhibited
Updated Date: 06-jun-2011
Creation Date: 26-nov-2010
Expiration Date: 26-nov-2011
>>> Last update of whois database: Thu, 01 Sep 2011 19:53:13 UTC <<<
…
…
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Registration Service Provided By: DOMAIN NAMES REGISTRAR REG.RU LTD.
Contact: +7.4955801111
Domain Name: RANDKIPL.COM
Registrant:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Creation Date: 26-Nov-2010
Expiration Date: 26-Nov-2011
Domain servers in listed order:
ns1.reg.ru
ns2.reg.ru
Administrative Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Technical Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Billing Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Status:LOCKED
Note: This Domain Name is currently Locked. In this status the domain
name cannot be transferred, hijacked, or modified. The Owner of this
domain name can easily change this status from their control panel.
This feature is provided as a security measure against fraudulent domain name hijacking.
— CUT —
Hm… All contact suggest the owner is somewhere in Australia (AU) but telephone number has prefix
to Denmark (+45). Of course name servers are in Russia 😉 Interesting is also STATUS of the domain:
— CUT —
Status:LOCKED
Note: This Domain Name is currently Locked. In this status the domain
name cannot be transferred, hijacked, or modified. The Owner of this
domain name can easily change this status from their control panel.
This feature is provided as a security measure against fraudulent domain name hijacking.
— CUT —
More information:
— CUT —
# host randkipl.com
randkipl.com has address 91.202.63.130
# host -t any randkipl.com
randkipl.com name server ns2.reg.ru.
randkipl.com name server ns1.reg.ru.
randkipl.com has address 91.202.63.130
# host 91.202.63.130
Host 130.63.202.91.in-addr.arpa. not found: 3(NXDOMAIN)
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the “-B” flag.
% Information related to ‘91.202.60.0 – 91.202.63.255’
inetnum: 91.202.60.0 – 91.202.63.255
netname: AKRINO-NET
descr: Akrino Inc
country: VG
org: ORG-AI38-RIPE
admin-c: IVM27-RIPE
tech-c: IVM27-RIPE
status: ASSIGNED PI
mnt-by: RIPE-NCC-END-MNT
mnt-by: MNT-AKRINO
mnt-lower: RIPE-NCC-END-MNT
mnt-routes: MNT-AKRINO
mnt-domains: MNT-AKRINO
source: RIPE # Filtered
organisation: ORG-AI38-RIPE
org-name: Akrino Inc
org-type: OTHER
address: Akrino Inc.
address: P.O.Box 146 Trident Chambers
address: Road Town, Tortola
address: BVI
e-mail: noc.akrino@gmail.com
mnt-ref: MNT-AKRINO
mnt-by: MNT-AKRINO
source: RIPE # Filtered
person: Igoren V Murzak
address: Akrino Inc
address: P.O.Box 146 Trident Chambers
address: Road Town, Tortola
address: BVI
phone: +1 914 5952753
e-mail: noc.akrino@gmail.com
nic-hdl: IVM27-RIPE
mnt-by: MNT-AKRINO
source: RIPE # Filtered
% Information related to ‘91.202.60.0/22AS44571’
route: 91.202.60.0/22
descr: AKRINO BLOCK
origin: AS44571
mnt-by: MNT-AKRINO
source: RIPE # Filtered
% Information related to ‘91.202.63.0/24AS44571’
route: 91.202.63.0/24
descr: AKRINO BLOCK #4
origin: AS44571
mnt-by: MNT-AKRINO
source: RIPE # Filtered
— CUT —
So Internet Service Provider is Akrino Inc. from Virgin Islands, British. If we google for this IP address we can discover that it was used many times for some attacks. Many domains was registered for this IP address, for example sex-v-odnoklassnikah.com, seks-v-mambe.com, sexnk.org, etc.
Here is nmap scan:
— CUT —
Nmap scan report for 91.202.63.130
Host is up (0.045s latency).
Scanned at 2011-09-02 00:43:47 CEST for 10s
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: OpenWrt White Russian 0.9 (Linux 2.4.30) (93%), OpenWrt 0.9 – 7.09 (Linux 2.4.30 – 2.4.34) (93%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (93%), Crestron XPanel control system (87%), Netgear DG834G WAP (87%), OpenBSD 4.3 (87%), Apple Mac OS X 10.6.2 – 10.6.4 (Snow Leopard) (Darwin 10.2.0 – 10.4.0) (86%), Cisco IronPort C650 email security appliance (AsyncOS 7.0.1) (86%), FreeBSD 6.1-RELEASE (86%), OpenWrt (Linux 2.4.30 – 2.4.34) (86%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=5.51%D=9/2%OT=80%CT=%CU=%PV=N%G=N%TM=4E600AAD%P=i686-pc-linux-gnu)
SEQ(SP=105%GCD=4%ISR=107%TS=U)
SEQ(SP=102%GCD=2%ISR=109%TI=RI%TS=U)
OPS(O1=M5B4SLL%O2=M578SLL%O3=M280%O4=M5B4SLL%O5=M218SLL%O6=M109SLL)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=40%W=2000%O=M5B4SLL%CC=N%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=N)
— CUT —
OK. It’s time to look a bit for the site. Here is headers from the connection:
— CUT —
http://randkipl.com/user.php?page=id&id=16112
GET /user.php?page=id&id=16112 HTTP/1.1
Host: randkipl.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pl,en-us;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://agagwhili.com/-lenaa
Cookie: view=1; p=336; sub=1887; sex=0; erotic=1; typep=0; PHPSESSID=a7a9a32d77f07a11d3b3cce52a7b2910
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 01 Sep 2011 19:24:43 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.2.17
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: view=1; expires=Fri, 02-Sep-2011 19:24:43 GMT; path=/
Set-Cookie: p=336; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: sub=1887; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: sex=0; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: erotic=1; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: typep=0; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
— CUT —
Server is in fact Apache in version 1.3.42 but the fake server name is transfered (nginx). Server use PHP/5.2.17 and create Cookies.
Next header:
— CUT —
http://randkipl.com/js/messages_pl.php?city=<city>
GET /js/messages_pl.php?city=<city> HTTP/1.1
Host: randkipl.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Accept: */*
Accept-Language: pl,en-us;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://randkipl.com/user.php?page=id&id=16112
Cookie: view=1; p=336; sub=1887; sex=0; erotic=1; typep=0; PHPSESSID=a7a9a32d77f07a11d3b3cce52a7b2910
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 01 Sep 2011 19:24:43 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.2.17
— CUT—
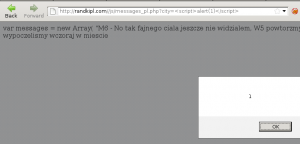
As we can see the city name is send to the server. This is what I wrote at the beginning. Site use this name to improve social engineering attack 😉
I didn’t have a time to lok for the site closer, but it has a lot of bugs in the registering form. Here is simple XSS:
In the cookies we can find information like chat box id, etc. 😉 Site was written probably by some russian guy – comments in the code suggest it:
$(‘#chat’).append(“<p><span>Гость</span> говорит:<br />”);
it means “Guess write”
<!–O mnie: <b>Моя красивая грудь всегда ждёт жарких чувственных поцелуев.
Я готова отдаться мужчине, который сможет своими опытными руками довести
меня до экстаза. Больше всего обожаю, когда меня берут сзади.</b><br>–>
I will not translate this 😉
About chat box. We can find it here:
http://randkipl.com//js/messages_pl.php?city=<city>
— CUT —
var messages =
new Array(
“M6 – No tak fajnego ciala jeszcze nie widzialem, W5 powtorzmy w nast. tygodniu?!\n”+
“W5 – Popatrzymy\n”+
“W2 – Dobrze wypoczelismy wczoraj w miescie <city>\n”+
“M12 – Hej! Starczy pornem sie bawic, kto wczoraj byl na spotkaniu grupowym w <city>? \n”+
“W2 – Ja bylam, chcesz powtorzyc? \n”+
“M12 – W2 no ze zdjec widac, ze niezle bylo, jestes taka mila ) \n”+
“M10 – Ci, ktorzy waslali swoje nagranie ‘W calym domu’ prosze podac link do strony brunetki, bardzo mi sie spodobala \n”+
“W5 – Wyslalam Ci do privu\n”+
“W28 – dla poczatku by nie zaszkodzilo. Zobaczyc kto czego wart. I u kogo jak stoi)))\n”+
“M1 – To oczym pytanie – zapraszam do priwu albo do web przez skype!\n”+
“W24 – Zgubilam wideo, to co wysylala W2? Prosze o podanie linku!\n”+
“M6 – M2 aktywnie wyklada swoje domowe wideo, nawet podejrzewam, ze zapraszali kogos filmowac)!\n”+
“M18 – Kto tam sie grozil zorganizowac striptiz przez skype?\n”+
“M19 – Starczy dreczyc, dziewczynki, wlaczajcie kamere! \n”+
“W24 – A kto mi obiecywal foto swojego ptaszka?\n”+
“W25 – W24 – A kto, do rzeczy, obiecywal?\n”+
“M12 – Jestem gotowy do spotkania z dziewczyna z Piteru!\n”+
“W5 – Juz zrzucilam Ci do priwu komorke – otrzymales?\n”+
“M6 – Kto uwielbia anal lesbijek, rzuce do priwu zajebisty filmik!\n”+
“W26 – Mam propozycje dla powaznych mezczyzn. Zapraszam do mego priwu! (miasto <b><city></b>)\n”+
“M10 – Co znaczy powaznych? Z kasa?\n”+
“W37 – Proponuje swoje realne intymne zdjecia\n”+
“W24 – Co za super! Z poczatku – no i potem koszmar, jak ona to wszystko wytrzyma?!))\n”+
“M19 – M7 – W2 w dzienniku ma taki ekstremalny, paluszki oblizesz! \n”+
“M1 – Aha. To ona tam sama chyba z dwoma facetami wystepuje, a wszystkim mowi, ze to jej kuzynka\n”+
“W2 – Namawiacie na skromna dziewczyne, niepotrzebnie)))\n”+
“W22 – W24 – Zajebiscie, co teraz zobaczylam z linku Sergieja. Popatrz!\n”+
“W41 – Proponuje realny seks z dominowaniem w Moskwie!\n”+
“M26 – czesc wszystkim. Jestem tu nowy. Naprawde tu zapoznywaja sie dla seksu, jestem z miasta<city>?\n”+
“W28 – Zalezy od tego, co proponowac bedziesz\n”+
“W28 – Czy myslales, ze przyslismy tutaj w miasta grac?))\n”+
“M26 – Poczatek optymistyczny, do rzeczy\n”+
“M26 – Samara. Jestem gotowy do spotkania dzis wieczorem z sympatyczna dziewczyna) \n”+
“M10 – Polina – dinamo. Dalej zdjec nie pojdzie!\n”+
“M9 – Kurde, dziewczynki, chce od razu dwoch – co robic?\n”+
“W5 – zobacz ankiete M11 – dwie siostry ;)\n”+
“W41 – M9 – Przyjezdzaj do mnie na Sokol w Moskwie, wszystko zalatwie. Szczegoly – w priwie!\n”+
“M10 – W41 powazna pani. Moze taaakie pokazac, juz widzialem!\n”+
“W37 – M6 – Hejki! Nie zdradzales mi tutaj?Ostatnim razem nasze spotkanie bylo nawet za bardzo!)\n”+
“M6 – zdradzalem z dwiema brunetkami i jedna piersiasta lesbi. Poczekaj, zaraz Ci Linki podam!\n”+
“W1 – Nie chlopaki poszli, a same masturbanty. Choc by ktos mi wsunal!)\n”+
“W30 – Oj, ja tez chce zobaczyc! M19, jestes z Moskwy?\n”+
“M19 – Tula! Proponuje dzisiaj grupowe spotkanie!\n”+
“W11 – co do seks-party w Tule zwracaj sie do mnie – w zeszlym miesiecu bylo niezle!\n”+
“W23 – Prosze i dla mnie troche czegoc slodziutkiego zostawic!)\n”+
“M9 – W2 – A jak Ci sie bardziej podoba?\n”+
“W2 – gdy w dupe, ale ostroznie! \n”+
“M18 – Starczy nakrecac, lepiej wyloz swoje nowe przygody w biurze!\n”+
“M26 – Popatrzcie w moim dzienniku na msj skarb i konczycie na siebie!\n”+
“W15 – Aha. Juz widzialam. Naprawde zachwyca! A to naprawde twoj?\n”+
“W1 – Ehe. Widzialam w realu, jeszcze wiekszy)))\n”+
“M1 – Gdy u niego wstaje, M26 pada!))))\n”+
“W26 – Kto chce nie przez skype – prosze do priwu po telefon i warunki!) \n”+
“M26 – M6 – A co, spotykales sie z Oksana?\n”+
“W10 – Patrzcie na ta rzecz. Krecili prosto na lekcji!\n”+
“M1 – Kurwa! Jak to oni wpali na sposob – prosto na podlodze!\n”+
“M21 – Tak, ciekawa poza, trzeba bedzie sprobowac!\n”+
“M24 – Starczy masturbowac, kto tam z <city> – przyjezdzajcie do mnie, pogramy w doroslych!\n”+
“W10 -M24 – telefon i zdjecie wyslij, moze i przyjade\n”+
“W5 – No jestem z <city>. A co umiesz?\n”+
“M24 – Co zechcesz – polize, anal, seks zabawki!\n”+
“W18 – Romka jest wielkim wymyslaczem! W sobote konczylam z nim 5 razy!)))\n”+
“M15 – A mi sie podobaja dziewczyny z piercingiem na wargach sromowych! Sa takie?\n”+
“W12 – Tutaj wszyscy takie!\n”+
“W27 – Aha, i nie tylko na wargach. Mam na pepku i jezyku pierscionek!\n”+
“M12 – Mowia, lody z piercingiem sa uajebiste! \n”+
“W22 – A ty co, nie probowalecs? To 7 niebo!\n”+
“M1 – M10 – Sluchaj, widziales W1 w realu?\n”+
“W1 – kto tu plotkuje o mnie? A psik!\n”+
“W5 – W2 – Popatrz-no, laseczko, na to! I to trzeba pod takim ujeciem zfilmowac! \n”+
“M12 – Prosze mi tez to pokazac, ocenie!\n”+
“W2 – WoW! Jak ona go tam wsunela?\n”+
“M6 – W11 – A ja o czym mowie? Rzucilem Ci do priwu link do bezoplatnego porno.\n”+
“W30 – A kto co wiecej lubi?\n”+
“M19 – ja uwielbiam lesbi z zabawkami)))\n”+
“W36 – Tak-tak, jak jedna druga straponem … – to superrrrrrr)))))\n”+
“W9 – Chce sie mezczyzny zywego – z penisem…\n”+
“M15 -W9 – Posluchaj, jak zrozumialem, jestes z Moskwy, to spotkajmy sie? \n”+
“W9 – Lap w priwie telefon!\n”+
“M24 – M7 – Zobacz, penisa dziewczynkom sie zechcialo. Moze pomozemy laseczkam? Zrobimy stoleczne swing-party? \n”+
“M7 – Tak zawsze za. W36, podaj numerek!\n”+
“W36 – M24 i M7 napiszcie do priwu!\n”+
“W35 – Popatrzcie, to ja z komorki swego chlopaka krecilam!\n”+
“W24 – Co za, jakiego ma miecza! Jak go przyjmujesz?\n”+
“W35 – Latwo!)))\n”+
“M26 – W48 – to Twoje wideo wysylal M2?\n”
);
function rand(l,k)
{
var rand_no = Math.random();
rand_no = l+rand_no * (k-l);
// alert(“”+rand_no+” “+Math.ceil(rand_no));
return Math.round(rand_no);
};
var rndnum = getCookie(‘curchattext’);
if (rndnum)
{
if ((rndnum<0) || (rndnum>=messages.length))
{
rndnum = rand(0, messages.length-1);
}
}
else
{
rndnum = rand(0, messages.length-1);
}
setCookie(‘curchattext’,rndnum);
//alert(rndnum);
var messagesArray=messages[rndnum].split(“\n”);
//alert(messagesArray.length);
var boys=new Array(
“dar”,
“michalkania”,
“Alex”,
“Amadeus”,
“Znieczulenie”,
“Andrzey”,
“Kamil”,
“Jakub”,
“Patrick”,
“Adrian”,
“Mihial”,
“David”,
“Katsper”,
“Mateus”,
“Ivan”,
“Marcin”,
“Daniel”,
“Shimon”,
“Bartlomieja”,
“Philip”,
“Christian”,
“Paul”,
“Adam”,
“Arkady”,
“Conrad”,
“Lukas”,
“Dariush”,
“Dominique”,
“Oscar”,
“Andrew”,
“Damian”,
“Przemyslaw”,
“Radoslav”,
“Rafal”
);
var boys_colors=new Array(
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“red”
);
var girls=new Array(
“Оля”,
“niunia”,
“aniaw”,
“Oliwia”,
“ania”,
“xxmartaxx”,
“milenka”,
“Katanyna”,
“Jana”,
“kari”,
“Emanuela”,
“Elica”,
“mi6kata”,
“krissito”,
“Zocha”,
“korona”,
“rainaxristovaa”,
“lusinda”,
“Mada”,
“Ewa”,
“Brygid”,
“Kunigunde”,
“Krysta”,
“Yalgonata”,
“Lidia”,
“Ingrid”,
“sensoria”,
“rosito”,
“justysia”,
“Grazyna”,
“pysia”,
“hotbeborana”,
“bebeto”,
“ognyanov”,
“treis”,
“LadyBetina”,
“crazyangel”,
“angel”,
“eli4ka”,
“lo6omomi4e”,
“niczky”,
“ledenataaaa”,
“aniaw”,
“justysia”,
“Krystyna”,
“Elwira”,
“Lodoiska”
);
var girls_colors=new Array(
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”
);
— CUT —
The name of the city is bold in the messages. This text are randomly put to the chat box with the random nick name. Of course we can post some java script code there instead of city 😉
Probably there is much more useful bugs. I didn’t register myself to play more, because I don’t have time to do that. If someone is interested in this topic and have some extra info please contact with me 😉
Best regards,
Adam Zabrocki
21
Jul
Finally! 19 of July 2011 I had defence of my Master of Degree. I pass exam from whole study at mark 5.5 (the highest mark) and defence my thesis with mark 5.5 (the highest mark) and on the diploma I’m going to have final mark 5.0 (almost the highest mark ;)). My thesis was interesting not only for me but also for my University and they want to send it to the contest 😉 My topic was: “Elaboration of an automatic system of fuzz testing technique to use in the CERN grid applications”. To be honest now I have very powerful fuzzer ;>
At the beginning of March I second time moved to Switzerland (because of my work at CERN). Before that I was working in Wroclaw Center for Networking and Supercomputing in security team. In the middle of one pentesting work me and my friends (Bartek Balcerek and Maciej Kotowicz) discovered very nice vulnerability in the TORQUE server.
TORQUE (Terascale Open-Source Resource and Queue Manager) is very common in any GRID projects – including GRID in European Organization for Nuclear Research aka CERN 🙂 By using this bug attacker are able to create dirty job and put it to the queue and server responsible for executing this job will be hacked. This is very dangerous situation from the infrastructure – in the easiest way noone else will be able to use GRID resources. In worst situation we are able to overtake control on the edge machine which can manipulate any other machine – of course server is running with the root privileges 😉
Here is advisory in full-disclosure list.
Here is backup on my server.
Best regards,
Adam Zabrocki
17
Nov
Finally! After few months of waiting we’ve got Phrack number 67! For me this is special release. Why? My article was accepted by Phrack staff and published at this release 🙂 I’m proud of that 😉 For me Phrack magazine is a legend. I grown on this magazine, so my connection with this magazine is even stronger 😉
At first I would like to thanks blackb1rd. He helps me very much with this article. If not blackb1rd, this article will never exists at this form like it is now. You’ve got beer from me, whenever we meet 😉
OK. So what about this release? Personally I think this is very good release. There is many interesting articles (for me). I love trick with exploiting user space vulnerabilities in the years of Non Executable Memory, ASLR, SSP, … and other shits 😉 There is Heap, there is Format Strings, and of course stack (my article), there is …. ah 😉
From the news the chapter ‘loopback’ comes back 😉 The full table of content is:
0x01 Introduction ....................................... Phrack Staff
0x02 Phrack Prophile on punk ............................ Phrack Staff
0x03 Phrack World News .................................. EL ZILCHO
0x04 Loopback (is back) ................................. Phrack Staff
0x05 How to make it in Prison ........................... TAp
0x06 Kernel instrumentation using kprobes ............... ElfMaster
0x07 ProFTPD with mod_sql pre-authentication ............ FelineMenace
0x08 The House Of Lore: Reloaded ........................ blackngel
0x09 A Eulogy for Format Strings ........................ Captain Planet
0x0a Dynamic Program Analysis and Software Exploitation . BSDaemon
0x0b Exploiting memory corruptions in Fortran programs .. Magma
under UNIX/VMS
0x0c PHRACKERZ: Two Tales ............................... Antipeace
&
The Analog Kid
0x0d Scraps of notes on remote stack overflow ........... pi3
exploitation
0x0e Notes Concerning the Security, Design and .......... The Philosopher
Administration of Siemens DCO-CS Digital
Switching Systems
0x0f Hacking the mind for fun and profit ................ lvxferis
0x10 International Scenes ............................... various
Pure content looks very interesting, so what is inside? 🙂 Go and read! Go Go GO!!! 🙂
Btw. As you see, my article is:
Scraps of notes on remote stack overflow
available here and backup on my site here.
Btw2. I’m waiting for feedback 😉
.
Best regards,
Adam Zabrocki
18
Mar
One day I was reviewing all bugs in bugtraq IDs (popular bids). I want to know which kind of bugs is it now popular and what is the trend of modern bugs. I came to two main conclusions:
1) The most popular are SQL/XSS bugs but in 60% this is found in software which nobody knows/uses (stupid kiddie)
2) We’ve got 2010 year and there is still possible to find stack overflow bugs! The most funny thing for me there is more remote stack overflow bugs than local 🙂
Stack overflow bugs is one of the oldest class of software bugs which still exists – more-less 10% of all bugs ! Of course it isn’t 199x year that you can find it using regexpression for ‘grep’ program. So what is conclusion? Exploit stack overflow bugs is still interesting from attackers point of view. The question is “Is it still possible to exploit this class of bugs in modern UNIX systems in 2010 year?”. The answer for this question isn’t simple. Let’s do simple review of modern defence systems. We’ve got:
*) Non-exec memory (not only stack – almost every region where it is NOT necessary) *) W^X – “Write XOR Exec” memory. It forbids memory with Write and Exec bits in the same time.*) AAAS – ASCII Armored Address Space *) ASLR – Address Space Layout Randomization *) mmap() and mprotect() protections
*) Heap protections – like safe-unlink(), safe malloc() implementation (OpenBSD) *) Random canary of death protections ——————————-|
*) frame pointer protection by canary of death |
*) move all pointers to the beginning of the frame |==> pro-police
*) move all local byte arrays to the end of the frame | protection (SSP) *) Vulnerable arguments copied to the local variables and then reordered—-| .
We can bypass most of this protection but if it isn’t connected. Is there any possibilities to exploit in modern UNIX systems REMOTE stack overflow bugs with enabled ALL of this protections?! It sounds crazy… but STILL we CAN DO IT 🙂 I wrote simple server with remote stack overflow bug and EXPLOIT it. Proof Of Concept of course is private but I created a movie of exploiting. You can find it here:
http://site.pi3.com.pl/priv/bypass-all-protections.flv
We’ve got 2010 year and we can still exploit remote stack overflow bugs in modern UNIX systems 🙂 Amazing… but it could be that this techniques (yes it isn’t one technique which is used to exploit this bug) is the last opportunity to exploiting remote stack overflow bugs… OK so… have a nice watching 🙂
Best regards,
Adam Zabrocki
30
Dec
This will be very short post… I have found (few months ago) security vulnerability in one of Apache server/module. I contact with apache security team. After few days I will decide about “future” of this bug – publish or wait for security path and publish after it. Now I can paste here simple output from gdb:
Program received signal SIGSEGV, Segmentation fault. 0x0000003fec682958 in memcpy () from /lib64/libc.so.6 Missing separate debuginfos, use: debuginfo-install expat-2.0.1-6.fc11.1.x86_64 glibc-2.10.1-5.x86_64 nss-softokn-freebl-3.12.4-3.fc11.x86_64 (gdb) bt #0 0x0000003fec682958 in memcpy () from /lib64/libc.so.6 #1 0x000000000043083c in inet_addr () #2 0x000000000042a796 in inet_addr () #3 0x000000000042975f in inet_addr () #4 0x000000000041d8f5 in inet_addr () #5 0x0000000000432a29 in inet_addr () #6 0x000000000044bc88 in inet_addr () #7 0x000000000044bceb in inet_addr () #8 0x0000000000441344 in inet_addr () #9 0x0000000000441521 in inet_addr () #10 0x00000000004416a7 in inet_addr () #11 0x0000000000441f5f in inet_addr () #12 0x0000000000442820 in inet_addr () #13 0x0000003fec61ea2d in __libc_start_main () from /lib64/libc.so.6 #14 0x0000000000403399 in inet_addr () #15 0x00007fffffffe618 in ?? () #16 0x000000000000001c in ?? () #17 0x0000000000000002 in ?? () #18 0x00007fffffffe87d in ?? () #19 0x00007fffffffe899 in ?? () #20 0x0000000000000000 in ?? ()
Best regards,
Adam Zabrocki
15
Dec
More than year ago I was publish advisory in ‘mtr’ software. I think, personally, it is great bug because it can’t exist without unspecified situation in libresolv library 🙂 The question is why have I written information about it on blog?
I forgot add this advisory in my site (sic!) 🙂 Now it’s ok and you can find this advisory here.
I attached to this advisory details and Proof Of Concept. If you haven’t read it yet i strongly recommend you to do it because it shows that sometimes if we read source code we think bug doesn’t exists but sometimes other external stuff/bugs/unspecified situation help us to trigger and exploit unexisting bug 🙂
Here is link – once again:
http://site.pi3.com.pl/adv/advisory-libresolv-mtr.txt
Btw. In future I want to continue research about CPU bugs and probably it will cause news posts in this topic 🙂
Best regards,
Adam Zabrocki
Last few weeks I was talking(mailing) with Derek (xpdf developer – btw. really nice guy) about some vulnerabilities in his product. 14th of October he published path for bugs (not only my vulnerabilites) so i decide to release advisory…