6
Dec
Is it a dream? Impossible? Bugs in CPU? No… it’s reality! CPU is only a piece of hardware. Everything have bugs… CPU too. I will give here only a piece of information about bugs in INTEL products…
From time to time Intel release erratas for his products! But not many people know about it and almost nobody read it 🙂 Last few years we had seen some kind of race in releasing new CPUs. Who release faster processor (AMD vs INTEL) and which processor will have more cores earlier. I think, personally, on one hand it is ok – we have faster processors and pay less money. In other hand I realize that the time which have company to test his products decrease. This situation always causes bugs in products.
On bugtraq list we can find ‘Theo de Raadt’s post about bugs in Intel Core 2 architecture – first post which sensitize this problem from OS security site. Here is piece of his post:
“These processors are buggy as hell, and some of these bugs don’t just
cause development/debugging problems, but will *ASSUREDLY* be
exploitable from userland code.”
You can find full post here.
It sounds really bad. Some of known bugs from 2006 are listed below:
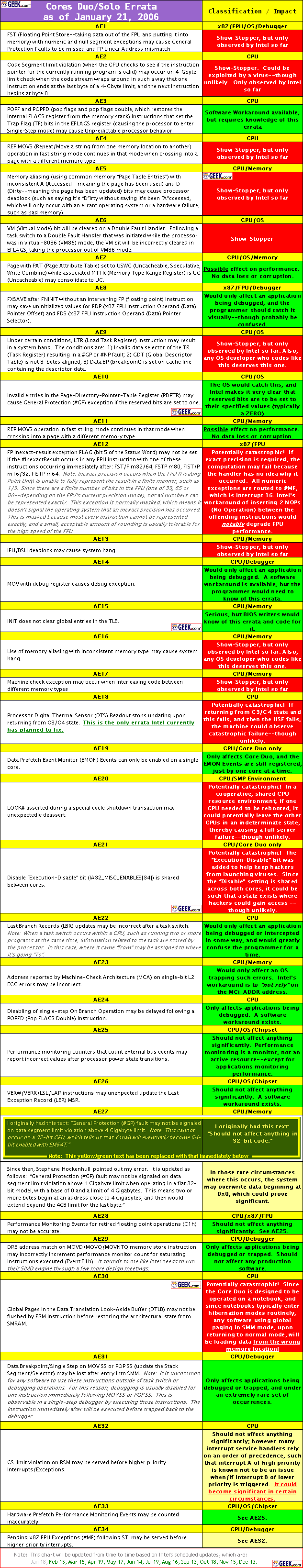
Yep. It looks amazing 🙂 Some of them can causes real security problem 🙂 Kris Kaspersky released his presentation about Intel CPU bugs. You can find it here.
For me the main point in this presentation is that he have got sample of virus which use one of CPU bugs to hide and exploit systems! Second important information is that he have received from this sample this piece of code which proof this bugs 🙂 Unfortunately he is not going to release it until Intel patch it ;/
Other interesting information is how it is possible (in theory) exploit some kind of Integer Overflow bugs in Unix systems – it is really interesting for me.
Let’s look for this piece of code:
foo(char *p, int len)
{
char buf[XXL];
…
if (len > XXL) return -1;
memcpy(buf, p, len);
return 0;
}
Third arigument for function memcpy() is ‘size_t’ type. In most systems size_t == unsigned int. If we pass negative value for ‘len’ variable proccess will crash. Minimum value for trigger this bug is 8000000h. On Windows it is exploitable via overwriting SEH structure but on *NIX systems like Linux it isn’t exploitable to code exec – in normal situation.
Bugs in CPU can cause this situation exploitable in system like Linux. What is scenario? When we trigger this software bug and processor start to overwriting memory when somehow we trigger on of CPU bug which will damage value in %ecx register than processor will stop overwriting memory (rep prefix?) and go to next instructions. Result of this scenario will be stop overwriting memory in situation when the process won’t be killed! It’s really interesting. I realize it is really hard to do but i think not impossible 🙂
What do you think? I’m waiting for comments…
Best regards,
Adam Zabrocki
Comments
Leave a Reply

Borys Łącki on 12.07.2009
Scary. Sometimes it is better not to know :]
Tweets that mention Exploitable CPU bugs… : pi3 blog -- Topsy.com on 12.08.2009
[…] This post was mentioned on Twitter by Mitchel Jhonson, thorkill. thorkill said: #cpu #bugs #exploits http://blog.pi3.com.pl/?p=55 (english is not perfect but hey why not) […]